Portfolio Details
Microsoft Active Directory Deployment
Price: 1200$
Duration: 2 weeks
01
introduction
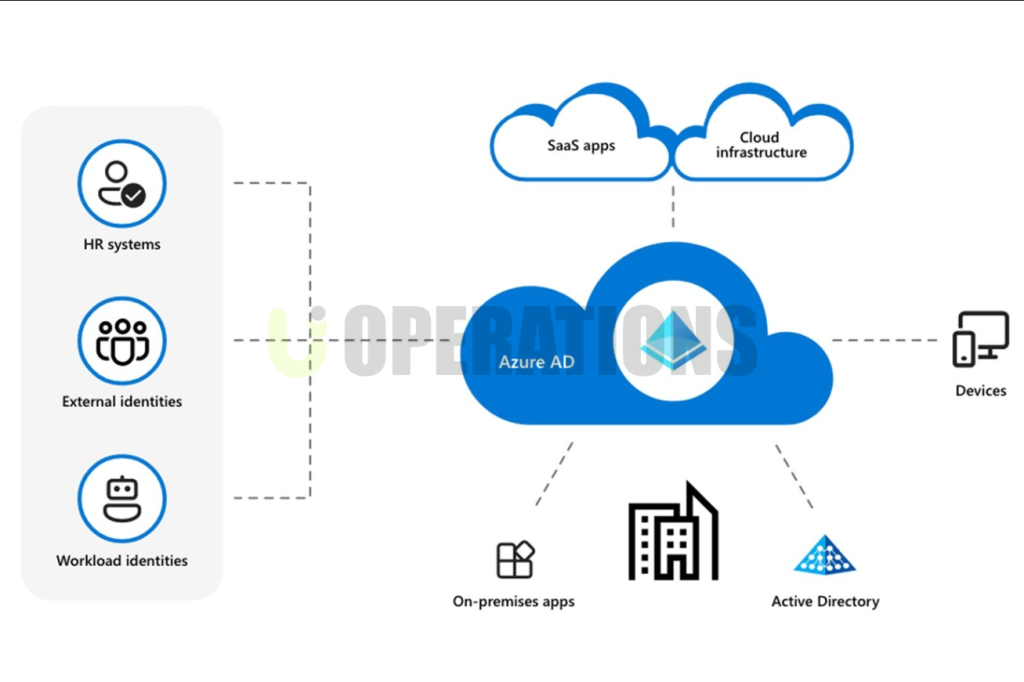
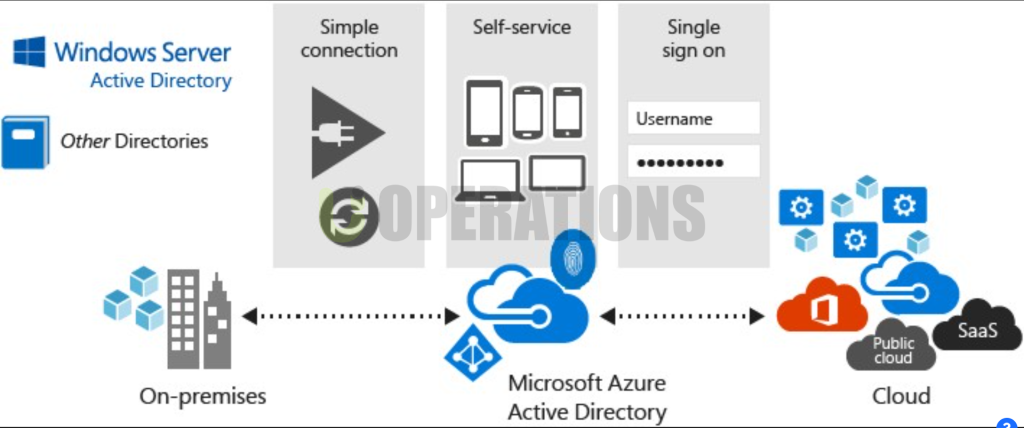
Microsoft Active Directory (AD) is a directory service that provides centralized management of network resources, including users, computers, and other networked devices. It is one of the most widely used directory services in enterprise environments, providing authentication, authorization, and management capabilities across IT infrastructures. AD allows businesses to organize their resources and implement security policies that ensure efficient, secure access to networked systems and applications.
As part of our efforts to streamline client IT management and enhance security, we were tasked with deploying Microsoft Active Directory for a client. The client’s goal was to modernize their IT infrastructure by consolidating user management, implementing a more secure authentication system, and setting up a solution that could scale as their organization grew. This document outlines the deployment process, key requirements, challenges faced, and the successful implementation of Active Directory for the client.
02
Client Requirements
Our client had specific requirements for the deployment of Active Directory. These were critical in guiding our approach and ensuring that the solution addressed their business needs. The client’s requirements were as follows:
- Centralized User Management
- The client needed a solution that would allow them to efficiently manage user accounts, groups, and access to resources from a single platform.
- The aim was to reduce administrative overhead and streamline the process of creating, updating, and disabling user accounts.
- Improved Security
- The client required an advanced security architecture to protect their sensitive business data.
- Features such as Multi-Factor Authentication (MFA), Group Policy Objects (GPOs), and secure login protocols (Kerberos) were essential in meeting the security standards.
- Scalability
- The client’s business had a significant presence in multiple locations and remote offices. They required a solution that could scale as the company expanded, both in terms of number of users and geographical reach.
- Active Directory’s ability to support multi-domain environments and replication between geographically dispersed Domain Controllers was crucial.
- Disaster Recovery and Redundancy
- The client wanted to ensure the availability of Active Directory in case of failures, ensuring that any disruption to their network could be quickly mitigated.
- A robust backup strategy, including System State backups and the establishment of additional Domain Controllers for redundancy, was required.
- Simplified Administration
- The client desired an administration process that was streamlined, automated, and easier to manage. This included self-service password resets, automated user provisioning, and simplified group management.
03
Deployment process
Our deployment of Microsoft Active Directory involved multiple stages, from planning to execution, and ultimately providing post-deployment support. Below is an overview of the key steps followed during the deployment.
- Planning and Assessment
The first step involved assessing the existing IT infrastructure and gathering the necessary information to inform the AD deployment. During this phase, we worked closely with the client to understand their current network architecture, security policies, and future growth plans.
Key actions taken during this phase:
- Infrastructure Assessment: We reviewed the client’s existing network setup to determine compatibility with Active Directory. This included evaluating server hardware, network topology, and the client’s current directory solution (if applicable).
- Requirement Gathering: We collaborated with the client’s IT team to define the project’s scope, identifying the number of users, locations, domains, and organizational units (OUs) needed. Additionally, we discussed the security features and automation goals they sought to implement.
- AD Design: We created an Active Directory design plan, including a detailed architecture for the domains, trust relationships, organizational units, and Group Policy Objects (GPOs).
- Installation and Configuration of Domain Controllers
With the planning phase complete, we began installing and configuring the first Domain Controller (DC) for the client. The Domain Controller serves as the central authentication point for users and machines in the domain.
Key steps involved:
- First Domain Controller Installation: The first DC was installed on a Windows Server, where we configured it as a Global Catalog and DNS server. This DC would serve as the primary hub for user authentication and resource access.
- Secondary Domain Controllers: To ensure redundancy and high availability, we deployed additional DCs in multiple physical locations. These DCs were configured to replicate with the primary DC, ensuring that the directory was available in case of failure.
- User and Group Management
User account creation and management are core functions in any Active Directory deployment. We designed the client’s Active Directory structure based on their organizational needs, using Organizational Units (OUs) to organize users by department or role.
Key actions taken:
- User Account Creation: We created user accounts for employees, assigning appropriate permissions and ensuring compliance with the client’s security requirements. This process involved integrating with HR systems to automate user account creation and updates.
- Group Management: We implemented groups to manage access control more effectively. These groups were organized by departments (e.g., Sales, HR, IT) to ensure that users were granted the correct access to resources.
- Role-Based Access Control (RBAC): We implemented RBAC to ensure that users were granted only the minimum level of access necessary for their roles. This helped reduce the risk of unauthorized access to sensitive data.
- Security Configurations
Security was a top priority for the client. As part of the deployment, we configured several security features to meet the client’s requirements for a secure network environment.
- Group Policy Objects (GPOs): We implemented GPOs to enforce security policies, such as password complexity, lockout policies, and login restrictions.
- Multi-Factor Authentication (MFA): To enhance security, we implemented MFA for critical accounts, requiring users to authenticate using both a password and a second factor (e.g., mobile device, biometrics).
- Secure Authentication Protocols: We ensured that Kerberos authentication was configured, along with other security protocols like LDAPS (LDAP over SSL) for secure communication between AD and other services.
- Replication and Redundancy
Active Directory replication ensures that changes made to one Domain Controller are propagated to others, maintaining consistency across the network.
Key actions:
- Replication Setup: We configured Active Directory replication between the Domain Controllers in different locations to ensure that user credentials and other directory information were consistent across all sites.
- Site and Subnet Configuration: We configured AD sites and subnets to optimize replication traffic, ensuring that replication occurred efficiently over the wide-area network (WAN).
- Redundancy and Failover: We tested the failover capabilities of the Domain Controllers to ensure that, in the event of hardware failure, the system would continue functioning without interruption.
- Backup and Disaster Recovery
A comprehensive backup and disaster recovery plan was developed to ensure that the client’s Active Directory environment could be restored in case of failure.
- Backup Strategy: We set up System State backups for the Domain Controllers, which include critical AD data like the Active Directory database and SYSVOL folder.
- Disaster Recovery Plan: We created a detailed disaster recovery plan that outlined the steps for restoring AD in the event of a failure. This plan included procedures for recovering individual Domain Controllers and restoring the entire Active Directory environment from backups.
04
Challenges Faced and Solutions
During the deployment, we encountered several challenges that required proactive problem-solving. These included:
- Integration with Legacy Systems: The client had older systems that were not fully compatible with modern authentication protocols. We addressed this by implementing appropriate trusts and ensuring backward compatibility during the migration process.
- User Migration: Migrating user accounts and data from the previous system to Active Directory proved complex. To mitigate this, we used the Active Directory Migration Tool (ADMT) to ensure a seamless transition, maintaining user profiles and permissions during the migration process.
- Security Configuration: Configuring MFA and ensuring that it worked across all platforms was a challenging task. We worked closely with the client to ensure that all systems were compatible with MFA, providing training and documentation to users to ensure smooth adoption.
05
conclusion
The successful deployment of Microsoft Active Directory met all the client’s requirements, providing them with a centralized, secure, and scalable solution for managing their IT infrastructure. The deployment process, from planning to post-deployment support, was tailored to ensure that the system was customized to the client’s needs, allowing them to improve security, enhance user management, and streamline IT operations.
The Active Directory solution is now fully operational, supporting multiple offices and remote users while maintaining high levels of security and availability. With the implementation of a disaster recovery plan and redundant Domain Controllers, the client can be confident that their AD environment will remain resilient in the face of challenges.

