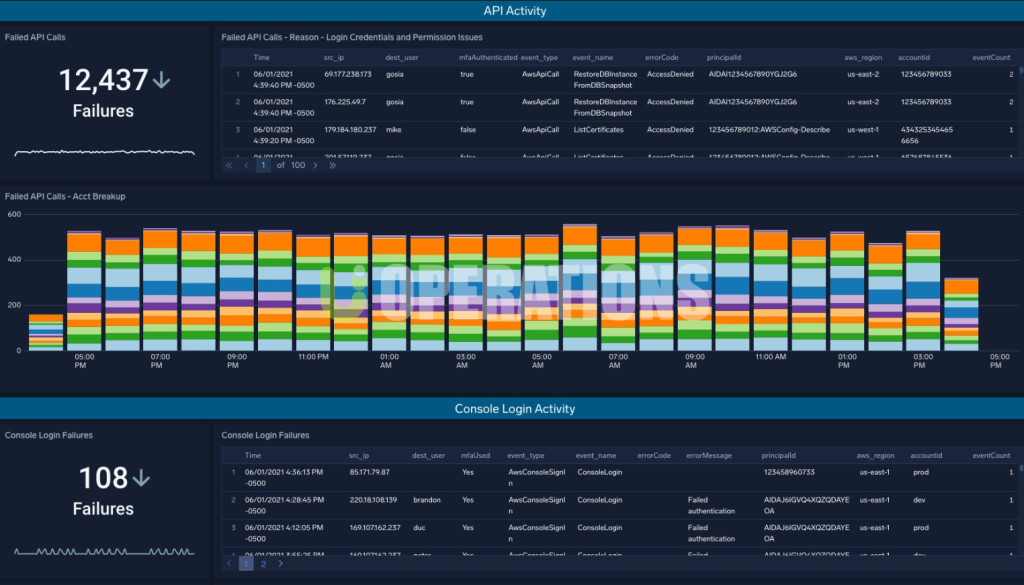
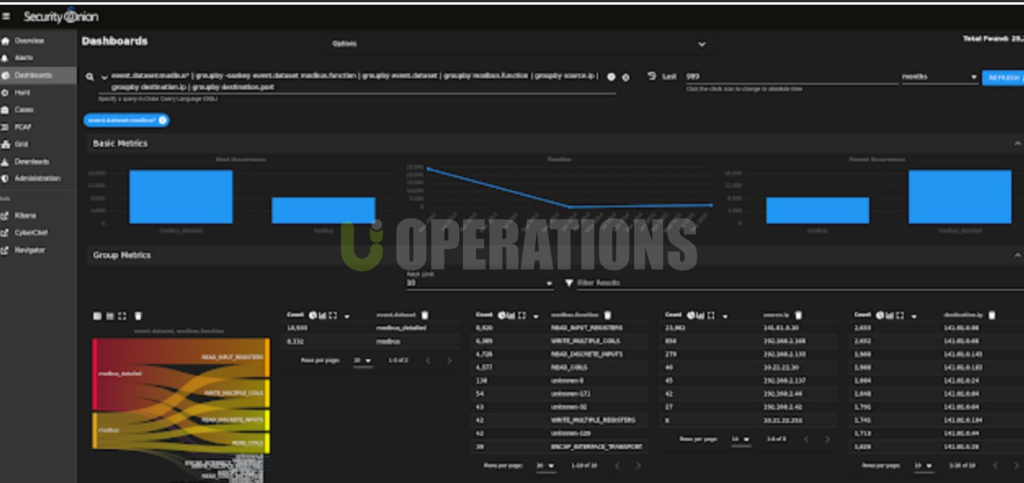
Portfolio Details
Security Onion Deployment
Price: 1500$
Duration: 2 weeks
01
Client Requirements
The client approached us with the need to deploy a comprehensive network security monitoring solution that could provide continuous monitoring, logging, and alerting for potential security incidents in their IT environment. The client required:
- Intrusion Detection System (IDS):
The client needed an IDS solution capable of detecting both signature-based and anomaly-based intrusions. This included the ability to monitor network traffic and provide detailed security alerts when suspicious activities were detected. - Network Traffic Analysis (NTA):
They required a system to analyze network traffic, identify patterns, and detect malicious behavior or abnormal traffic. This needed to be integrated with their existing network architecture. - Centralized Logging:
The client wanted a centralized log management solution that would aggregate logs from different devices (firewalls, servers, routers) and provide a unified view of security events and incidents. - Security Incident Response:
The client sought a platform that could help with both detection and response to security incidents, enabling them to investigate suspicious activities and respond in real-time. - Scalability and High Availability:
The solution needed to scale to support a growing network infrastructure and ensure high availability for continuous security monitoring without interruption.
- Intrusion Detection System (IDS):
02
Solution Delivered
To address the client’s requirements, we deployed Security Onion, an open-source, comprehensive Linux-based platform for intrusion detection and network security monitoring. The deployment was broken down into the following key steps:
- Security Onion Installation and Configuration
We deployed Security Onion on a dedicated server or virtual machine using the following steps:
- Operating System Installation:
Security Onion can be deployed on a variety of Linux distributions. We selected Ubuntu for its compatibility with the tools in Security Onion and the client’s existing infrastructure. - Security Onion Setup:
We followed the Security Onion setup guide to deploy the operating system and associated security tools. The installation process included:
- Choosing the Deployment Type: Security Onion offers various deployment types (Standalone, Distributed, and High-Availability). For this client, we chose a distributeddeployment to handle the scale and redundancy requirements.
- Deployment Size: Based on the client’s network size and traffic volume, we determined the appropriate hardware resources for each component of Security Onion (e.g., the Elasticsearch cluster, Suricata IDS/IPS sensors, and Zeek network analysis nodes).
- Intrusion Detection System (IDS) and Network Security Monitoring (NSM)
Suricata and Zeek were deployed for intrusion detection and network security monitoring:
- Suricata IDS/IPS:
We deployed Suricata on each network sensor to detect network intrusions based on both signature-based and anomaly-based techniques. Suricata provided real-time analysis of network traffic, including packet captures and threat alerts.
- Signature-based Detection: Suricata used existing signature databases to identify known attack patterns.
- Anomaly Detection: Suricata also provided anomaly detection capabilities to identify deviations from normal network behavior.
- Zeek (formerly known as Bro):
Zeekwas deployed as a complementary tool to Suricata. Zeek specializes in providing deeper analysis of network traffic and creating detailed logs of network connections, protocol usage, and potential attacks.
- Zeek (formerly known as Bro):
- Protocol Analysis: Zeek analyzed various network protocols, including HTTP, DNS, and FTP, to identify suspicious traffic.
- Event Correlation: Zeek generated logs for network traffic, which were forwarded to Elasticsearch for deeper analysis and querying.
- Centralized Logging with Elastic Stack
Security Onion uses the Elastic Stack (Elasticsearch, Logstash, and Kibana) for centralized logging and data analysis:
- Elasticsearch:
Elasticsearchwas used as the storage backend for all logs generated by Suricata, Zeek, and other Security Onion components. We set up a dedicated Elasticsearch cluster to handle the large volume of security event data.
Indexing and Searching: Elasticsearch indexed logs for fast searching, allowing security analysts to query and correlate logs quickly to identify potential incidents.
Logstash:
Logstash was configured to process and forward log data to Elasticsearch. We set up the necessary filters and parsers to clean and normalize log data from various sources (e.g., Suricata, Zeek, firewalls, servers).
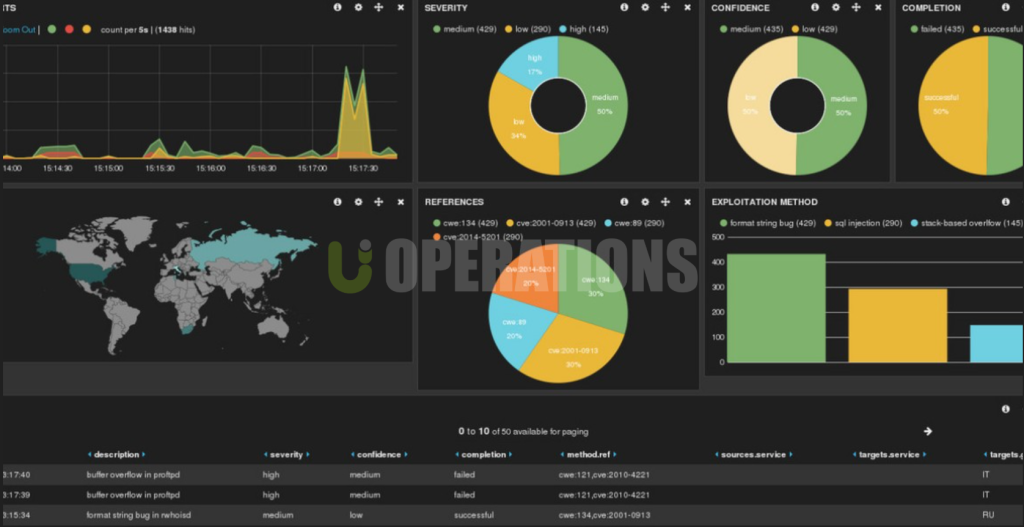
- Kibana:
Kibana was deployed as the web interface for visualizing and analyzing logs. We created several custom dashboards in Kibana to allow the client to view real-time network activity, intrusion alerts, and security event trends.
- Alert Dashboards: Dashboards were created for real-time alert monitoring, providing a quick overview of active security events.
- Trend Analysis: Kibana was used to analyze historical data and identify long-term security trends.
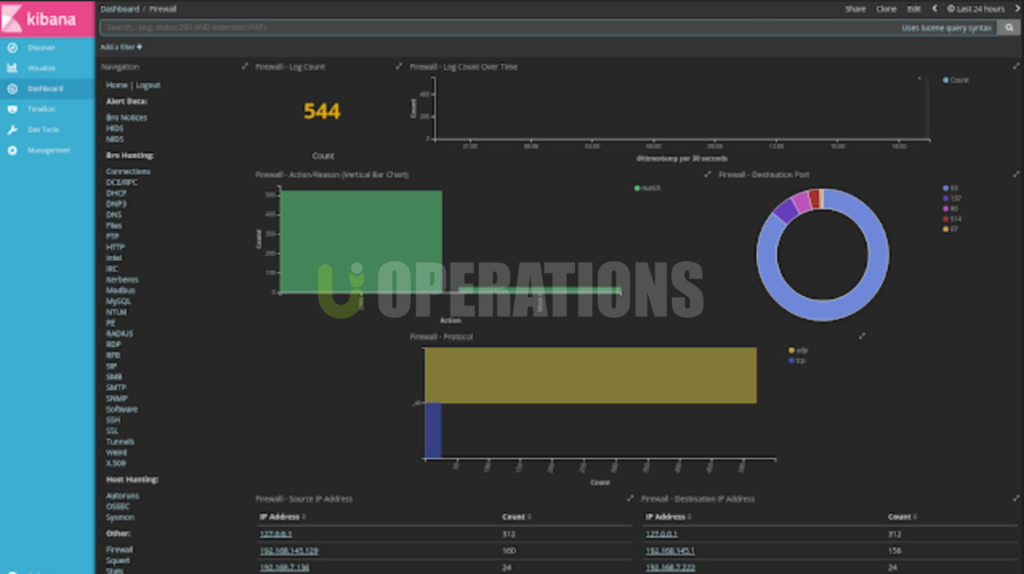
- Security Incident Response and Analysis
Security Onion provides a comprehensive platform for security incident response:
- Security Event Correlation:
We configured event correlation rules to automatically link related alerts from Suricata, Zeek, and other sources. This helped reduce the volume of alerts by grouping similar events and providing context for further investigation. - Alert Management:
We set up alert notifications using Elastic Stack’s alerting capabilities, ensuring that the security team was notified of critical incidents in real-time. Alerts were integrated with external communication tools like Slack and Email to ensure timely responses. - Investigation and Forensics:
The Security Onion platform provided full packet capture (PCAP) capabilities, allowing the security team to perform in-depth forensics on network traffic. This helped in investigating incidents and determining the scope and impact of attacks.
- High Availability and Scalability
To ensure high availability and scalability, we implemented the following:
- Distributed Deployment:
We deployed Security Onion components in a distributed manner to handle large amounts of data and provide redundancy. Components like Elasticsearch and Suricata were deployed across multiple servers to balance the load and ensure uptime. - Data Redundancy:
Elasticsearch was set up with replica indices for data redundancy and high availability. This ensured that data would be available even if one of the Elasticsearch nodes went down. - Horizontal Scaling:
We designed the solution with the ability to scale horizontally. Additional Suricata sensors, Zeeknodes, and Elasticsearch nodes could be added easily as the client’s network grew, ensuring continued monitoring without performance degradation.
- Security and Access Control
- Role-Based Access Control (RBAC):
We configured RBAC in Kibana to restrict access to sensitive logs and dashboards based on the user’s role. For example, the security team had full access to all logs and alerts, while other teams had limited access to specific dashboards. - SSL/TLS Encryption:
We enabled SSL/TLS encryption for all communications between Security Onion components to ensure data privacy and integrity.
03
Key Achievements
- Comprehensive Intrusion Detection:
The deployment of Suricata and Zeek ensured that the client had comprehensive network security monitoring with real-time intrusion detection and traffic analysis. - Centralized Security Data:
The use of the Elastic Stack provided the client with a centralized log management system, enabling easy access to, and analysis of, security event data from across the network. - Real-Time Alerts:
Configuring real-time alerting ensured that the security team was notified immediately when suspicious activity was detected, allowing for rapid response.
- Comprehensive Intrusion Detection:
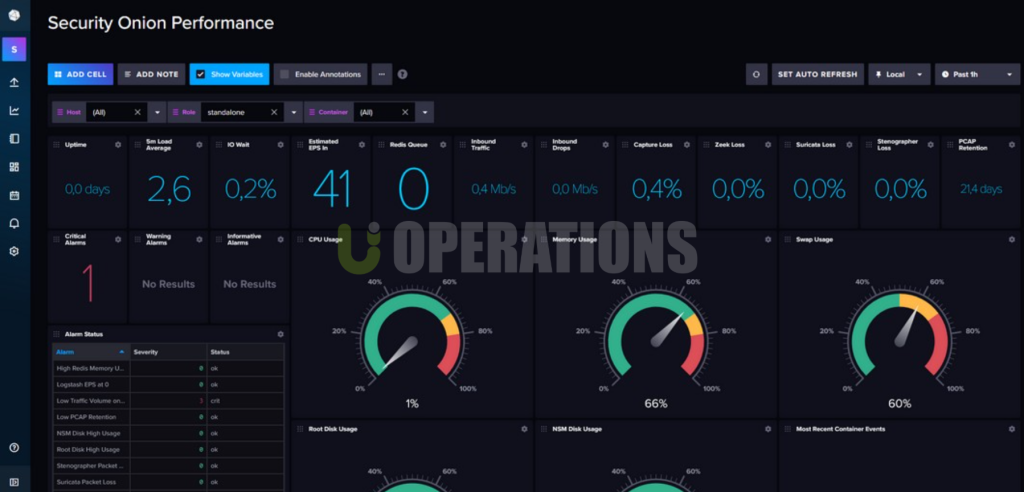
- Scalable and High Availability:
The solution was designed for scalability, with horizontal scaling in place to support the growing network infrastructure. High availability was achieved with redundant components and data replication.
- Scalable and High Availability:
04
Challenges Overcome
- Complex Network Traffic:
The client had a complex network infrastructure with diverse protocols and communication patterns. We overcame this by fine-tuning Zeek and Suricata configurations to ensure comprehensive traffic analysis. - Data Volume Management:
Handling the large volume of logs and metrics generated by network traffic required careful setup of Elasticsearch indices and data retention policies to ensure system performance while managing storage. - Alert Fatigue:
Reducing the volume of false positives and providing meaningful alerts was crucial. We fine-tuned alert thresholds and used event correlation to ensure that only critical alerts were raised.
- Complex Network Traffic:
05
Technologies & Tools Used
- Security Onion: Intrusion detection, network traffic analysis, and log management platform.
- Suricata: Intrusion Detection and Prevention System (IDS/IPS).
- Zeek: Network monitoring and traffic analysis tool.
- Elastic Stack (Elasticsearch, Logstash, Kibana): Centralized logging, storage, and visualization.
- Kibana: Data visualization and dashboarding tool.
- Ansible: Used for automation and configuration management.
- Docker: Used for containerized deployment of specific components, if required.
06
OUTCOMES
The Security Onion deployment provided the client with a comprehensive, scalable solution for continuous network monitoring, intrusion detection, and security event management. The solution enabled the security team to detect, investigate, and respond to security incidents in real-time, with high availability and ease of scaling for future growth.
07
Conclusion
This Security Onion deployment successfully delivered a robust and scalable security monitoring solution, integrating intrusion detection, network traffic analysis, and centralized logging. The system was fully configured for real-time alerts, historical analysis, and incident response, empowering the client’s security team to detect and mitigate security threats effectively.