Portfolio Details
Palo Alto Networks Deployment on Google Cloud Platform (GCP)
Price: 1000$
Duration: 2 weeks
01
Introduction
Palo Alto Networks (PAN) is a leading provider of cybersecurity solutions, offering comprehensive protection for networks, endpoints, cloud environments, and more. By leveraging PAN solutions on Google Cloud Platform (GCP), organizations can ensure robust security, scalability, and high availability in their cloud-based infrastructure.
This document outlines the deployment and integration process of Palo Alto Networks solutions on GCP, meeting a client’s specific security requirements and ensuring seamless operation within their cloud environment.
02
Client Requirements
The client, a growing enterprise with critical cloud workloads hosted on GCP, sought a comprehensive cybersecurity solution that could address their specific cloud security needs. Their requirements included:
- Cloud-Native Security: The client required a solution that could operate in a cloud-native environment and integrate seamlessly with Google Cloud services to protect their workloads in real-time.
- Centralized Security Management: The client wanted a centralized way to monitor, manage, and control all security aspects of their GCP infrastructure, without adding unnecessary complexity.
- Scalable Protection: With their expanding GCP infrastructure, the client required a solution that could scale horizontally to handle the growing number of virtual machines (VMs) and services in their cloud environment.
- Network Segmentation and Micro-Segmentation: The client sought enhanced network segmentation capabilities to isolate different environments within their GCP infrastructure, improving security by limiting lateral movement in the event of a breach.
- Automation and Orchestration: The client wanted the ability to automate security tasks, including threat detection and response, as well as integrate with their existing DevOps processes for continuous deployment and automation.
- Integration with Google Cloud Native Services: The client required a seamless integration of Palo Alto Networks’ solutions with native GCP services such as Google Kubernetes Engine (GKE), Google Cloud Storage, and Compute Engine.
- Comprehensive Threat Intelligence: As part of the security strategy, the client wanted access to real-time threat intelligence to better understand and mitigate potential risks within their GCP infrastructure.
03
Deployment Process
- Pre-Deployment Planning
The deployment process began with a comprehensive review of the client’s GCP architecture, security needs, and existing tools. This phase focused on understanding how Palo Alto Networks’ solutions could complement their existing cloud setup and address their specific requirements.
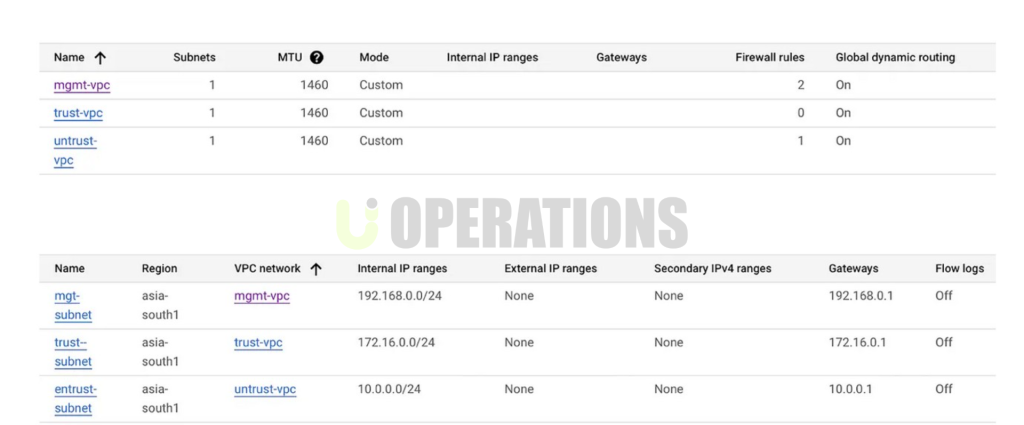
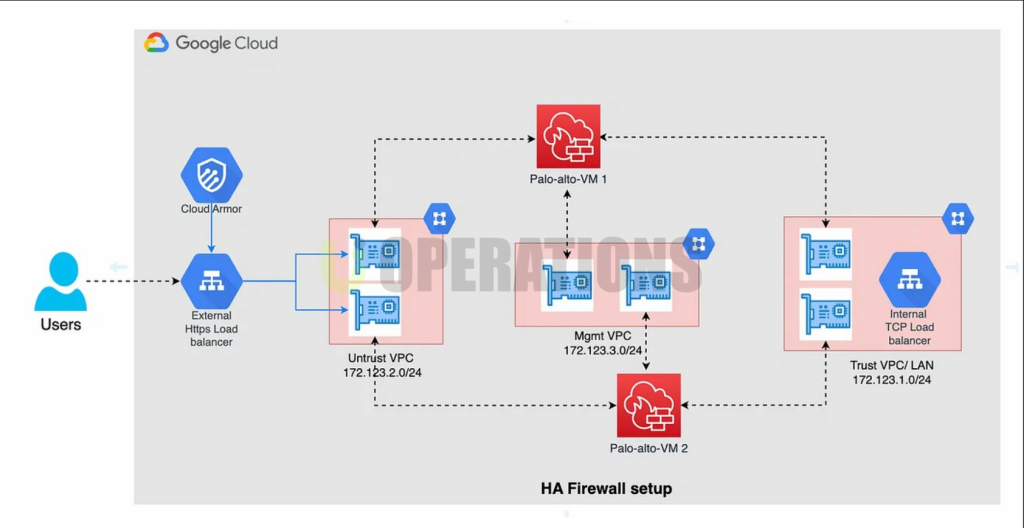
- GCP Infrastructure Review: A detailed assessment of the client’s GCP environment was carried out, including the architecture of their VPCs (Virtual Private Cloud), subnets, firewall rules, and other network configurations.
- Security Policy Design: The client’s security team worked with Palo Alto Networks experts to design security policies and controls based on best practices for cloud security.
- Requirement Mapping: We mapped the client’s requirements (such as scalable protection, micro-segmentation, and centralized management) to the capabilities offered by Palo Alto Networks.
- Solution Selection and Configuration
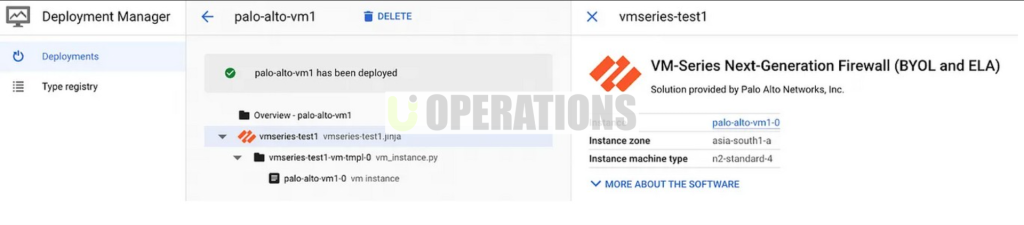
For the client’s needs, we selected Palo Alto Networks VM-Series firewalls for their cloud-based security platform on GCP. The VM-Series provides advanced firewall capabilities, such as traffic inspection, threat prevention, and URL filtering, with the flexibility to scale on-demand in the cloud environment.
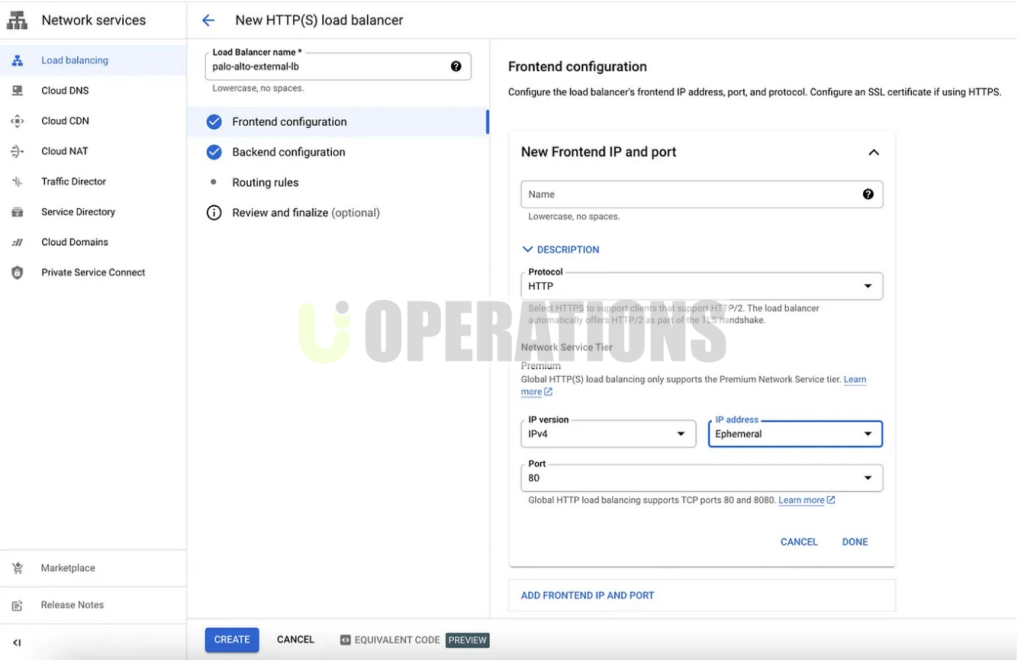
- VM-Series Firewall Deployment: The VM-Series firewall was deployed as virtual appliances within the GCP environment. These firewalls were configured to secure traffic flowing between the client’s GCP subnets and external networks.
- Virtual Private Cloud (VPC) Design: Security policies were configured to establish a secure and segmented network architecture within GCP. Subnets were segmented based on the client’s business units, and communication between these segments was restricted to reduce the risk of lateral movement.
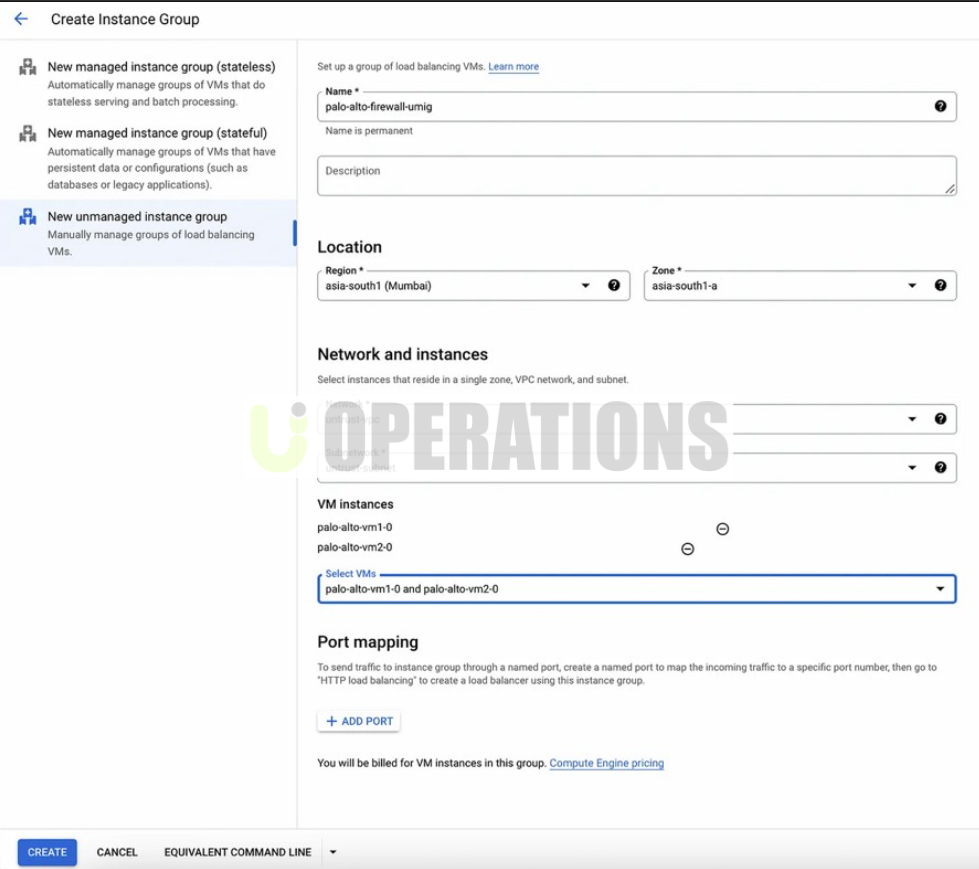
- Automated Scalability: Palo Alto Networks solutions were integrated with GCP auto-scaling features, ensuring that firewall and security capabilities scaled automatically with the increasing demand on the client’s cloud infrastructure.
- GKE and Kubernetes Security: Integration with Google Kubernetes Engine (GKE)was enabled to provide container-level security, ensuring that the client’s containerized workloads were secure from network-level threats and vulnerabilities.
- Integration with Google Cloud Native Services
Palo Alto Networks solutions were integrated with key Google Cloud services to ensure seamless security coverage for all workloads and services in the client’s environment:
- Cloud Storage: Palo Alto Networks security policies were applied to Google Cloud Storage, ensuring that data in transit and at rest was protected against unauthorized access or exfiltration.
- Identity and Access Management (IAM): Integration with GCP IAM policies was configured to enforce least-privilege access to resources within the client’s environment, ensuring secure identity and access management.
- Cloud Functions & Automation: GCP Cloud Functions were utilized to automate security response actions, such as quarantining compromised instances, based on threat intelligence data received from Palo Alto Networks threat feeds.
- Centralized Security Management
To streamline management and visibility, Palo Alto Networks’ Panorama management platform was deployed to provide a centralized view of the client’s cloud security posture. Panorama offers real-time visibility into the health and activity of the VM-Series firewalls and integrates with other security tools to improve incident response and compliance.
- Log Integration with Google Cloud Logging: All firewall logs were integrated with Google Cloud Loggingfor centralized monitoring, making it easier for the client’s security team to analyze security events.
- Policy Management: The security team could create, modify, and push security policies from a centralized platform, improving operational efficiency and reducing the likelihood of misconfigurations.
- Testing and Validation
After configuration, the deployed solution underwent rigorous testing to validate its functionality and security posture.
- Traffic Simulation: The team ran simulated attack scenarios to ensure that the Palo Alto Networks firewalls correctly detected and blocked malicious traffic.
- Performance Testing: Testing was performed to ensure that the VM-Series firewalls could handle the expected traffic volume and scale automatically based on demand.
- Compliance Check: The solution was reviewed to ensure that it met industry compliance standards, such as GDPRand PCI-DSS, given that the client stored sensitive data in their GCP environment.
- Training and Knowledge Transfer
To ensure the client could fully leverage the Palo Alto Networks solution, comprehensive training was provided to the client’s security and operations teams:
- Firewall and Security Policy Management: Security administrators were trained to manage the Palo Alto Networks firewalls and configure security policies effectively.
- Incident Response: The security team learned how to utilize Panorama and Google Cloud’s native tools to respond to security incidents promptly and efficiently.
- Automation Tools: The team received training on using GCP’s automation tools alongside Palo Alto Networks for continuous monitoring and security event response.
- Ongoing Support and Optimization
Post-deployment support included continuous monitoring and periodic optimizations to ensure the solution’s effectiveness:
- Security Health Monitoring: Continuous health checks of the firewalls and security configurations were implemented to identify and resolve any security gaps.
- Policy Tuning: As the client’s GCP environment grew, security policies were periodically updated to address new threats and evolving business needs.
04
Key Benefits Delivered
- Scalable Cloud Security: The VM-Series firewalls provided scalable and flexible security for the client’s growing GCP infrastructure, ensuring comprehensive protection without performance degradation.
- Cloud-Native Threat Protection: By integrating with GCP’s native services, Palo Alto Networks provided seamless security across the client’s cloud workloads, including VMs, Kubernetes, and storage.
- Centralized Management and Monitoring: Panorama provided a single pane of glass for managing and monitoring all security aspects of the client’s GCP environment, improving operational efficiency.
- Enhanced Network Segmentation: The deployment of security policies ensured that traffic between different GCP subnets was tightly controlled, reducing the attack surface and enhancing network segmentation.
- Automated Security Operations: Automated threat detection, response, and security policy enforcement helped the client minimize manual intervention and reduce response times to security events.
05
Conclusion
The deployment of Palo Alto Networks solutions on Google Cloud Platform successfully addressed the client’s security needs, ensuring comprehensive protection for their cloud workloads. Through seamless integration with GCP services, centralized management, and automated security capabilities, the client now benefits from a robust, scalable, and secure cloud infrastructure.