Portfolio Details
Palo Alto Networks Deployment on Amazon Web Services (AWS)
Price: 1000$
Duration: 2 weeks
01
Introduction
Palo Alto Networks (PAN) provides advanced cybersecurity solutions that protect against sophisticated cyber threats across networks, endpoints, and cloud environments. Deploying PAN solutions on Amazon Web Services (AWS) allows organizations to leverage the scalability, flexibility, and resilience of the cloud while ensuring robust security for their AWS infrastructure.
This document outlines the deployment and integration of Palo Alto Networks solutions on AWS, highlighting the specific requirements of the client and detailing the steps taken to meet those needs.
02
Client Requirements
The client, an organization utilizing AWS for its cloud-based infrastructure, needed a comprehensive solution to safeguard their AWS workloads. Their specific requirements included:
- AWS Cloud-Native Security: The client wanted a security solution that was designed to operate in an AWS-native environment and seamlessly integrate with AWS services.
- Scalability: With increasing cloud resources, the client required a solution that could scale dynamically with their AWS environment, providing robust protection without sacrificing performance.
- Centralized Security Management: The client needed a centralized platform to manage security policies, analyze logs, and monitor security across their AWS environment in real time.
- Network Segmentation and Micro-Segmentation: They sought the ability to segment their AWS environment, controlling traffic between different Virtual Private Cloud (VPC) segments, and enforcing granular security policies to limit lateral movement in case of a breach.
- Integration with AWS Security Services: The client required integration with AWS security services, including AWS Security Hub, AWS CloudTrail, and AWS Lambda, to enhance threat intelligence, automation, and compliance reporting.
- Cost-Effective Protection: Given the client’s cloud-first strategy, they wanted a security solution that was flexible and cost-effective, with the ability to scale resources dynamically without significant overhead.
- Threat Prevention and Visibility: They needed real-time threat prevention and visibility into network traffic, especially with the increasing use of containers and microservices within their AWS environment.
03
Deployment Process
- Pre-Deployment Planning
The deployment process began with an in-depth review of the client’s existing AWS infrastructure and security posture. We worked with the client’s security team to understand their environment, business goals, and security objectives.
- AWS Infrastructure Review: A review of the client’s AWS environment, including VPCs, subnets, security groups, IAM (Identity and Access Management) policies, and any existing security services (e.g., AWS WAF, Shield).
- Requirement Mapping: We mapped the client’s requirements to the Palo Alto Networks solutions, ensuring that the deployment would address specific needs such as AWS-native security integration, scalability, and centralized management.
- Security Policy Design: Palo Alto Networks experts worked with the client’s team to design security policies tailored to the AWS environment, ensuring that traffic flows between services and VPCs were appropriately secured.
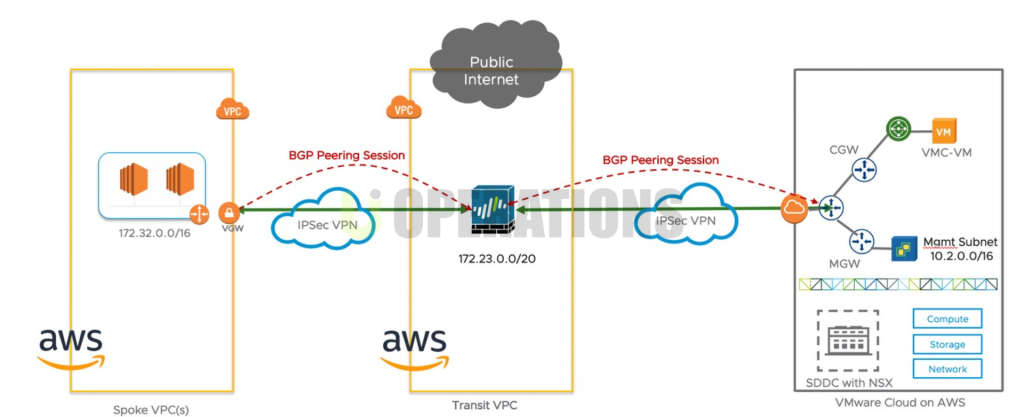
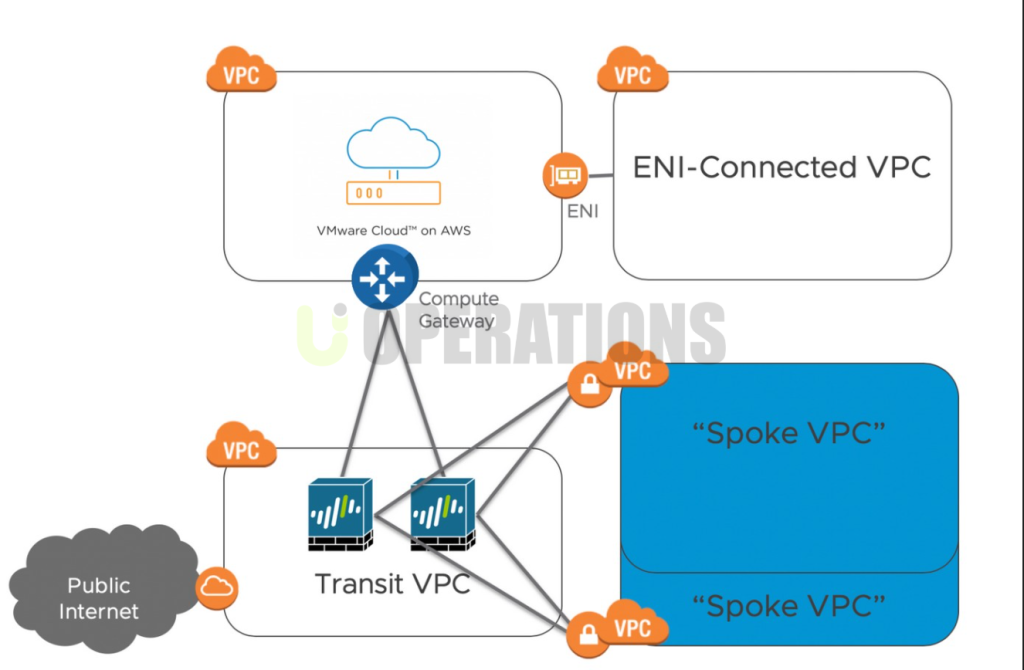
- Solution Selection and Configuration
For the client’s requirements, we deployed Palo Alto Networks VM-Series firewalls on AWS. The VM-Series provides advanced security features, including traffic inspection, threat prevention, URL filtering, and more. These firewalls were configured to protect the client’s AWS workloads, including EC2 instances, VPCs, and containerized environments.
- VM-Series Firewall Deployment:
- The VM-Series firewalls were deployed as Amazon Machine Images (AMIs)in the AWS environment, providing elastic scalability and high availability.
- The firewalls were set up within AWS VPCsto secure network traffic between subnets, control access to critical resources, and prevent unauthorized traffic from entering or leaving the environment.
- Elastic Load Balancing (ELB): The firewalls were configured to work in conjunction with AWS Elastic Load Balancing, ensuring that traffic was distributed efficiently across the deployed firewalls, supporting high availability and fault tolerance.
- Auto-Scaling Configuration: To ensure that security scales with the growing demand on the client’s cloud infrastructure, AWS Auto Scalingwas configured to automatically scale the Palo Alto Networks firewalls based on traffic volume and workload changes.
- VPC Peering: VPC peering was set up between different VPCs to secure inter-VPC traffic using Palo Alto Networks firewalls, ensuring that all communication between cloud environments was protected by next-gen firewall capabilities.
- Integration with AWS Security Services
Seamless integration with AWS native security services was key to meeting the client’s requirements:
- AWS Security Hub: The VM-Series firewalls were integrated with AWS Security Hubto centralize the security alerts and findings from Palo Alto Networks and other AWS-native services. This enabled a unified view of the client’s security posture.
- AWS CloudTrail and CloudWatch: Logs from the Palo Alto Networks firewalls were integrated with AWS CloudTrailand CloudWatch, enabling real-time monitoring and visibility into traffic flows, threats, and firewall actions.
- AWS Lambda: To automate incident response, the Palo Alto Networks deployment was integrated with AWS Lambda. In case of a detected threat, the system could automatically trigger Lambda functions for tasks like quarantining compromised instances, scaling firewall resources, or initiating remediation workflows.
- Network Segmentation and Micro-Segmentation
The client required robust network segmentation and micro-segmentation capabilities within AWS to ensure that security was enforced between workloads and application tiers. The following measures were implemented:
- Network Security Policies: Palo Alto Networks firewalls were configured with security policies to control traffic between different subnets within the same VPC, as well as between different VPCs. This restricted unauthorized access and reduced the impact of potential breaches.
- Micro-Segmentation: Using the VM-Series’ capabilities, we implemented micro-segmentationfor workloads such as EC2 instances and containers in AWS. This allowed the client to isolate critical application components and apply more granular security policies.
- Centralized Management with Panorama
To provide visibility and control over the entire AWS deployment, Palo Alto Networks Panorama was deployed for centralized security management.
- Policy Management: All security policies were managed centrally through Panorama, allowing the security team to make changes across multiple AWS environments without having to configure each VM-Series instance individually.
- Log Aggregation and Analysis: All firewall logs were aggregated in Panorama, allowing the client’s security team to analyze security events, track traffic flows, and perform detailed reporting. Panorama’s integration with AWS CloudWatch further enhanced this functionality.
- Automated Policy Updates: Security policies were automatically updated to reflect new requirements or changes in the AWS environment, ensuring continuous protection.
- Testing and Validation
After the initial configuration, extensive testing was conducted to ensure that the solution met the client’s requirements:
- Traffic Simulation: We simulated various attack scenarios, including DDoS, port scanning, and unauthorized access attempts, to test the effectiveness of the firewall rules and security policies.
- Scalability Testing: We tested the scalability of the deployment by increasing traffic volumes and ensuring that AWS Auto Scaling correctly scaled the Palo Alto Networks firewalls to meet demand without performance degradation.
- Compliance and Security Health Check: The deployment was reviewed for compliance with the client’s security requirements and industry standards such as PCI-DSSand GDPR.
- Training and Knowledge Transfer
Training was provided to the client’s IT and security teams on the proper use and management of Palo Alto Networks solutions on AWS.
- Firewall and Policy Management: Training was conducted on how to configure, manage, and optimize firewall policies.
- Incident Response: The security team was trained on how to leverage AWS-native tools in combination with Palo Alto Networks to automate incident response workflows.
- Logging and Reporting: The client’s team was instructed on how to analyze logs in AWS CloudWatchand Panorama, ensuring they could quickly identify and respond to threats.
- Ongoing Support and Optimization
Post-deployment, ongoing support was provided to ensure the system remained secure and optimized.
- Continuous Monitoring: Regular monitoring and alerting were set up through AWS CloudWatchand Panorama, ensuring that security events were quickly identified and addressed.
- Security Audits: Periodic security audits were scheduled to assess the effectiveness of the deployed security policies and to identify any gaps.
04
Key Benefits Delivered
- Scalable Security: The solution scales dynamically to handle increased workloads in AWS, ensuring that security adapts as the client’s infrastructure grows.
- Centralized Management: Panorama provided a single point of management for all Palo Alto Networks firewalls deployed across multiple AWS accounts and VPCs.
- Advanced Threat Prevention: The VM-Series firewalls delivered advanced threat prevention, including deep packet inspection, IPS, URL filtering, and DNS security, protecting the client’s workloads from sophisticated threats.
- Seamless Integration with AWS: The integration with AWS-native services such as Security Hub, CloudTrail, and Lambdaenabled automated responses and centralized visibility.
- Enhanced Network Segmentation: The deployment enabled the client to enforce strict network segmentation policies within AWS, reducing lateral movement and improving security.
05
Conclusion
The deployment of Palo Alto Networks solutions on AWS successfully addressed the client’s security needs, providing comprehensive protection for their cloud workloads. Through advanced features such as automated scalability, centralized management, and seamless AWS integration, the solution delivered a robust, secure, and cost-effective security architecture for the client’s AWS environment.

