Portfolio Details
Cisco Firepower Threat Defense (FTD) Security Integration
Price: 1350$
Duration: 2 Weeks
01
Client Requirement
Our client required an advanced security solution to protect their network against an increasingly complex landscape of cyber threats. Given the sensitivity of their business operations, they needed a solution based on Cisco Firepower Threat Defense (FTD), ensuring robust protection across their infrastructure. The key requirements for this project included:
- Comprehensive Threat Detection and Prevention:
The client needed a solution that would provide advanced intrusion prevention, malware detection, and zero-day protection to safeguard their network infrastructure against both external and internal threats. - Network Segmentation and Access Control:
They wanted to enforce secure network segmentation to isolate critical assets and ensure that only authorized traffic could reach sensitive systems. Additionally, they needed access control policies to protect data and resources. - Advanced Malware Protection and Visibility:
The client wanted visibility into both known and unknown threats. They needed advanced malware protection (AMP) to analyze and detect malicious files and prevent malware from spreading across their network. - Secure Remote Access and VPN Support:
The client required a solution that would enable secure remote access for employees while ensuring that their traffic was encrypted and threats were blocked, even when working from outside the corporate network. - Centralized Security Management:
The client needed centralized management and reporting capabilities to streamline the monitoring of security incidents, enforce policies across multiple sites, and gain detailed insight into potential threats.
- Comprehensive Threat Detection and Prevention:
02
Solution Delivered
To meet the client’s complex security requirements, we implemented Cisco Firepower Threat Defense (FTD), a next-generation security solution designed to provide advanced threat protection, network visibility, and unified management. This included a combination of Cisco NGFWs, intrusion prevention, malware protection, and secure remote access.
- Cisco Firepower Threat Defense (FTD) Deployment:
Cisco FTD was deployed across the client’s network perimeter to act as a next-generation firewall. The FTD platform provided:
- Advanced Threat Protection: Integrated Intrusion Prevention System (IPS) with Advanced Malware Protection (AMP), enabling detection of both known and unknown threats and preventing malware from entering or spreading within the network.
- Application Visibility and Control (AVC): Provided granular control over applications based on user identity, application type, and traffic patterns, preventing unauthorized applications from running on the network.
- Deep Packet Inspection (DPI): Enabled full inspection of all traffic, including encrypted traffic, to detect and block any malicious content attempting to infiltrate the network.
- Intrusion Prevention System (IPS) Configuration:
Cisco FTD’s IPSmodule was configured to monitor all network traffic for potential attacks and vulnerabilities. The system included:
- Intrusion Prevention System (IPS) Configuration:
- Zero-Day Attack Prevention: Using real-time threat intelligence feeds to identify new and emerging attack vectors, protecting the network from the latest exploits.
- Customizable IPS Policies: IPS policies were customized to ensure that traffic originating from high-risk sources or suspicious behavior was immediately flagged and blocked.
- Cisco Firepower Threat Defense (FTD) Deployment:
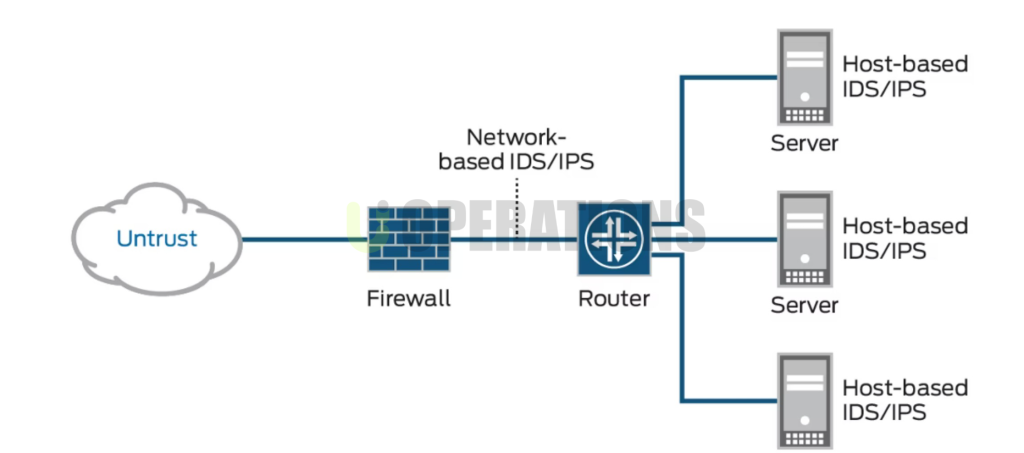
- Advanced Malware Protection (AMP):
Cisco FTD was integrated with Cisco AMP, which provided:
- File Reputation Analysis: Real-time analysis of files to identify malicious files or patterns of behavior indicative of malware.
- Continuous File Monitoring: Continuous monitoring of files and endpoints to detect and remediate malware that may have bypassed traditional defenses.
- Cloud-based Malware Analysis: Leveraged Cisco’s Threat Intelligence Cloudfor deep malware inspection and analysis, enabling rapid responses to new malware outbreaks.
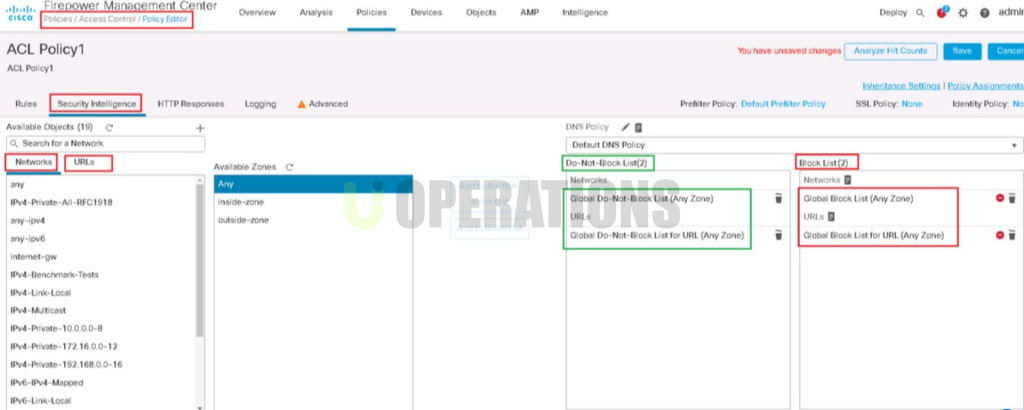
- Network Segmentation and Access Control:
We implemented secure network segmentation using Cisco FTD’s policy enforcement capabilities. This ensured that:
- Network Segmentation and Access Control:
- Critical assetswere isolated in secure zones with access controlled based on pre-defined policies.
- Access Control Lists (ACLs)were configured to ensure that only authorized users and systems could access sensitive information and applications.
- Identity and User-based Policieswere enforced with integration to Cisco Identity Services Engine (ISE), which provided detailed visibility into users and devices, enhancing policy enforcement.
- Advanced Malware Protection (AMP):
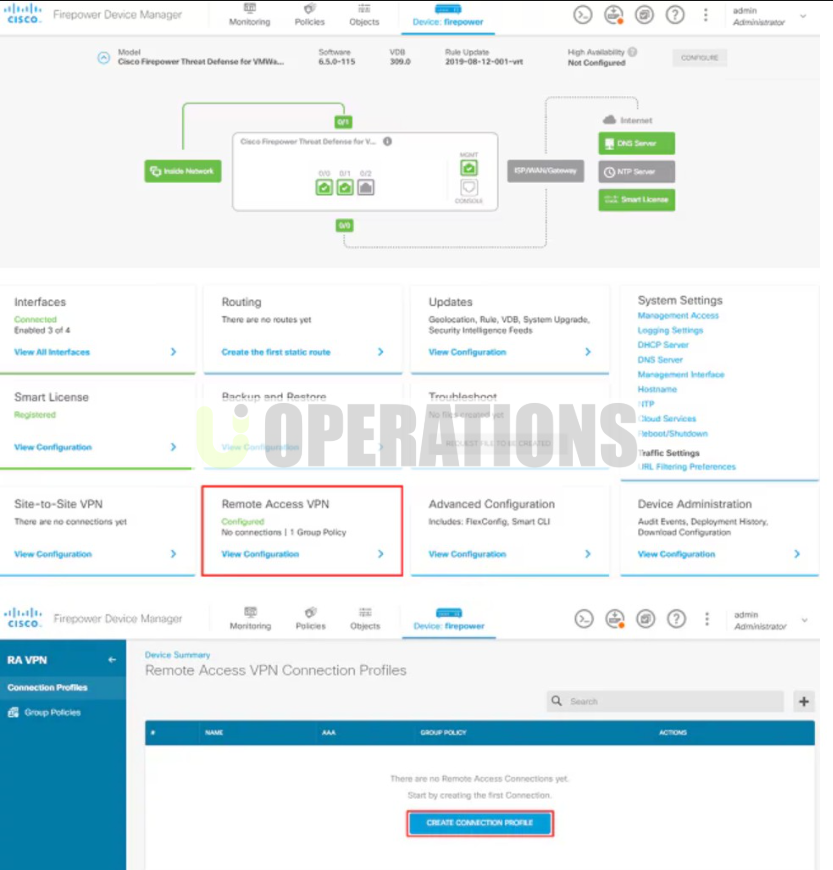
- Secure Remote Access with VPN:
The client’s remote workforce needed secure access to the corporate network. We deployed Cisco AnyConnect VPN integrated with Cisco FTD, which offered:
- Secure Remote Access: Allowed employees to securely connect to the corporate network via SSL VPNor IPSec VPN, ensuring that all traffic was encrypted and protected from eavesdropping.
- Endpoint Compliance Checks: Integrated with Cisco AMPand Cisco ISE to ensure that only compliant devices could access the network, reducing the risk of infections from unmanaged devices.
- Granular Access Control: Allowed access based on user role, device status, and location, ensuring the right people had the right access to the right resources.
- Secure Remote Access with VPN:
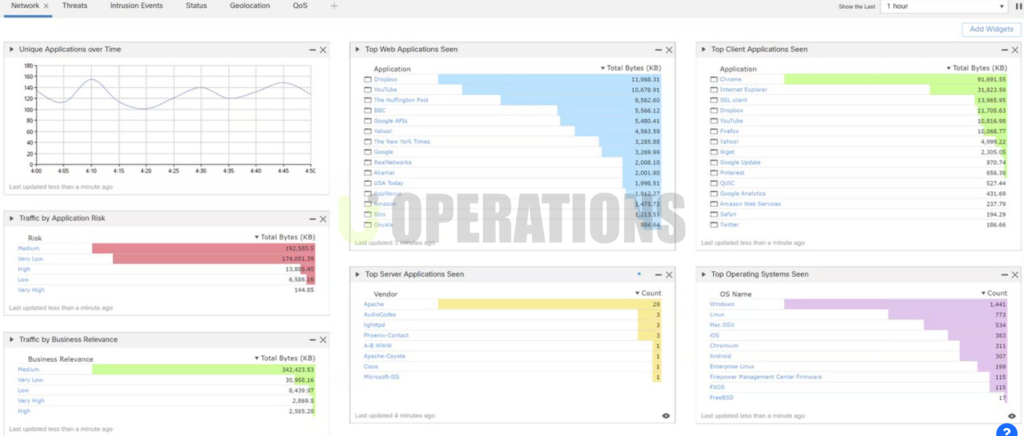
- Centralized Management with Cisco Security Management Center (SMC):
To manage the security environment, we implemented Cisco Security Management Center (SMC) to provide:
- Centralized Policy Management: Simplified configuration and deployment of security policies across the client’s entire network, including remote offices and data centers.
- Security Monitoring and Reporting: Enabled real-time visibility into the network’s security posture with detailed logs, alerts, and reporting capabilities.
- Automated Incident Response: Integrated automated response capabilities to respond to security events quickly, including quarantining infected devices and blocking malicious traffic.
- Centralized Management with Cisco Security Management Center (SMC):
03
Key Achievements
- Comprehensive Threat Detection and Prevention:
The Cisco FTD solution provided advanced intrusion prevention, real-time malware detection, and application visibility across the client’s network, ensuring robust protection against evolving cyber threats. - Secure Remote Access:
With Cisco AnyConnect VPN and Cisco AMP integration, the client’s remote workers were able to securely access the corporate network without compromising the security of their endpoints or data. - Network Segmentation and Access Control:
The implementation of secure network segmentation and identity-based policies ensured that critical assets were protected, and only authorized users could access sensitive resources. - Centralized Security Management:
Using Cisco SMC, the client gained centralized control over all security operations, ensuring that policies were consistently enforced and security incidents could be quickly identified and addressed.
Scalability:
The Cisco FTD solution provided a scalable architecture that could grow with the client’s expanding network, ensuring that additional users, devices, and remote locations could be securely integrated- Comprehensive Threat Detection and Prevention:
04
Challenges Overcome
- Complex Network Integration:
Integrating Cisco FTD across multiple locations and ensuring seamless communication between security devices required careful planning and configuration. We ensured consistent policy enforcement and traffic inspection, regardless of the network’s complexity. - Remote Worker Security:
Securing remote access for a large, distributed workforce required deploying Cisco AnyConnect and integrating it with endpoint compliance checks. This ensured that only authorized and secure devices could access the network, even from outside corporate offices. - Zero-Day Attack Prevention:
Preventing zero-day attacks required integrating real-time threat intelligence with the Cisco FTD platform. We successfully deployed automatic updates and threat signatures, allowing the system to stay ahead of emerging threats.
- Complex Network Integration:
05
Technologies & Tools Used
- Cisco Firepower Threat Defense (FTD): Next-Generation Firewalls (NGFW), Intrusion Prevention System (IPS), Advanced Malware Protection (AMP), Deep Packet Inspection (DPI), Application Visibility and Control (AVC)
- Cisco AnyConnect VPN: Secure SSL VPN and IPSec VPN, Endpoint Compliance
- Cisco Security Management Center (SMC): Centralized Policy Management, Monitoring, and Incident Response
- Cisco Identity Services Engine (ISE): Identity and Access Management
- Cisco AMP: Malware Protection, Threat Intelligence Cloud
06
Outcome
By the end of the project, the client achieved the following:
- A highly secure network with comprehensive protection against both internal and external cyber threats.
- Secure remote access for employees through Cisco AnyConnect VPN, ensuring encrypted connections and endpoint security.
- Centralized security management via Cisco SMC, providing real-time visibility and efficient policy enforcement across the entire infrastructure.
- A scalable, resilient security environment capable of growing alongside the client’s network infrastructure while maintaining security integrity.
07
Conclusion
The Cisco Firepower Threat Defense (FTD) solution successfully met the client’s security needs by providing advanced threat prevention, comprehensive network visibility, and centralized management. The deployment strengthened the client’s network defense, ensuring robust protection against cyber threats, optimized secure remote access, and simplified security management.

