Portfolio Details
Cisco Firepower Threat Defense (FTD) High Availability (HA) Deployment
Price: 850$
Duration: 2 Days
01
Project Overview
We were engaged by our client to deploy a High Availability (HA) solution using Cisco Firepower Threat Defense (FTD) 4100 Series firewalls to ensure network redundancy, fault tolerance, and continuous uptime. The client required a solution that would minimize downtime during maintenance, provide resilience in case of hardware failure, and maintain security policy enforcement across the network. Our task was to configure and implement an Active/Standby HA pair of Cisco FTD firewalls to meet the client’s business continuity and security needs. This project involved planning, designing, implementing, and rigorously testing the solution to ensure that the network infrastructure met the client’s operational requirements.
02
Project Objectives
The primary objectives for this deployment were:
- Network Redundancy:Our client required a solution that would ensure network availability even during hardware failure or maintenance downtime. The solution was designed around an Active/Standby HA configuration to ensure continued firewall protection and traffic flow.
- Minimal Downtime:The client emphasized the importance of achieving seamless failover between the two firewalls to minimize service disruptions.
- Security Policy Consistency:Ensuring that the client’s security policies and network configurations were consistently enforced across both firewalls during failover events was a key requirement.
- Scalability:The client wanted a solution that could scale to accommodate future growth, allowing for the addition of more devices without impacting performance or network availability.
03
Pre-Deployment Planning
Site Survey & Requirements Gathering:
- Current Network Architecture Review:We first assessed the client’s existing network architecture, reviewing the configuration of their current firewall and identifying critical areas that would benefit from high availability.
- Stakeholder Interviews:We worked closely with the client’s network and security teams to gather detailed HA requirements, such as acceptable failover times, specific load balancing needs, and policies to be enforced.
- Device Selection:Based on the client’s performance and security needs, we selected the appropriate Cisco FTD models, such as the Cisco Firepower 2100 or 4100 series, to ensure the chosen devices met both capacity and throughput requirements.
Design & Architecture:
- High Availability Topology:We designed an Active/Standby HA configuration for the Cisco FTD firewalls. In this setup, the Active unit processes traffic while the Standby unit remains idle but ready to take over in case of failure.
- HA Requirements:
- Redundant Management Interfaces:We ensured both firewalls had redundant management interfaces to maintain uninterrupted access for remote management and monitoring.
- HA Ports and Sync Links:We configured dedicated HA ports for synchronization between the two devices to ensure reliable communication and data replication.
- Session Synchronization:The HA setup was configured to synchronize sessions between the two firewalls to prevent disruption during failovers.
- IP Addressing & Routing:
- Floating IPs:Floating IP addresses were configured to ensure automatic failover, allowing the Standby firewall to take over the Active firewall’s IP address in case of failure.
- Routing Protocols:We implemented dynamic routing protocols (e.g., OSPF or BGP) to ensure automatic route convergence and traffic rerouting during failovers.
- HA Configuration:Configured synchronization for security policies, network settings, and session data across both firewalls. Health monitoring was implemented to detect any failures and trigger failover.
04
Deployment
Step 1: Hardware & Software Setup
- Firewall Installation:We physically installed two Cisco FTD firewalls (e.g., Cisco Firepower 2100 or 4100 series) in the client’s data center to serve as the Active and Standby units.
- FTD Software Version:We deployed the latest stable version of Cisco Firepower Threat Defense (FTD) software to take advantage of the latest HA features.
- Initial Configuration:
- Configured management interfaces with static IPs for remote access.
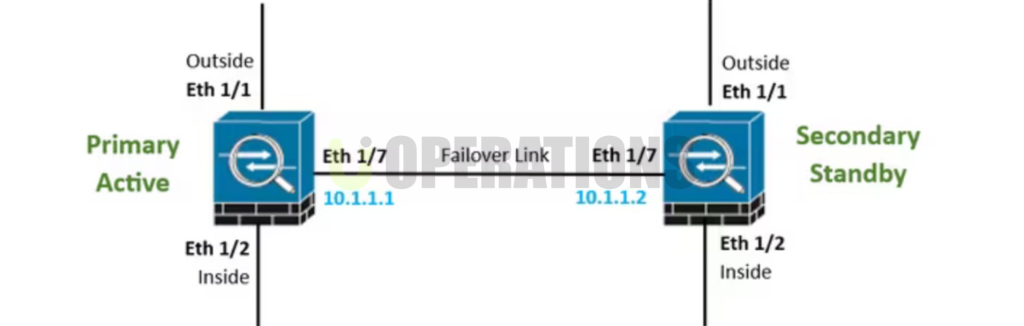
- Established the HA link between the firewalls using dedicated HA ports, ensuring synchronization capabilities.
- Verified that both devices were running the same version of FTD software and were correctly synchronized.
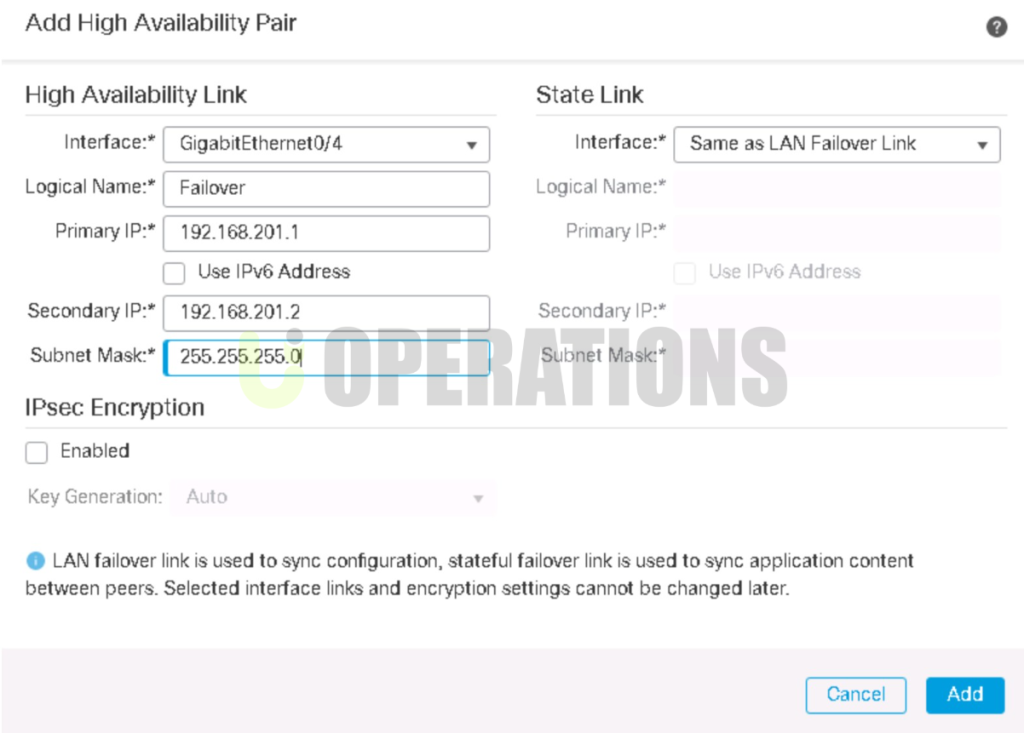
Step 2: HA Configuration
- HA Pairing:We configured the HA pair by establishing communication between the Active and Standby firewalls using the dedicated HA link and ensured synchronization of settings and policies.
- HA Mode Selection:Active/Standby mode was selected, where only the Active firewall handles traffic, and the Standby firewall remains passive, ready to take over if the Active firewall fails.
- Session Sync & Stateful Failover:We configured session synchronization to ensure that active sessions were maintained during failover, allowing uninterrupted network activity.
- Health Monitoring:Health monitoring was configured to regularly check the status of system components, network interfaces, and the synchronization link, allowing automatic failover in the event of hardware or network failure.
Step 3: Policy and Rule Configuration
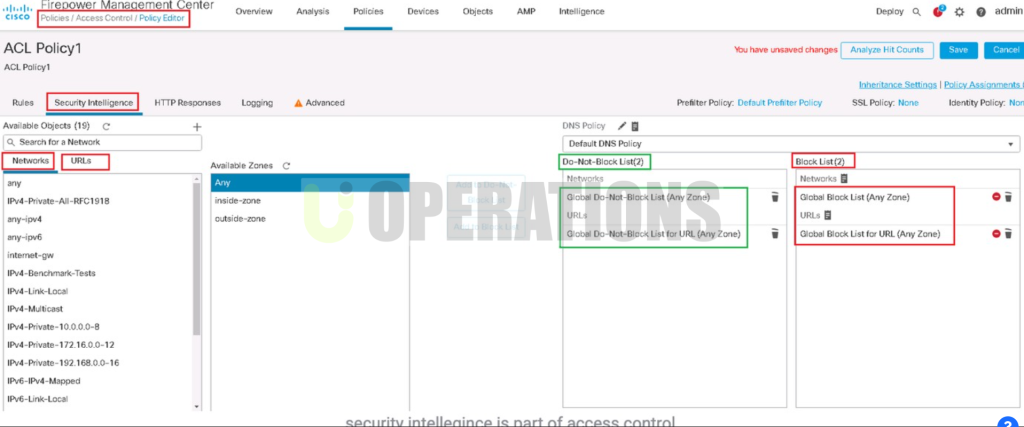
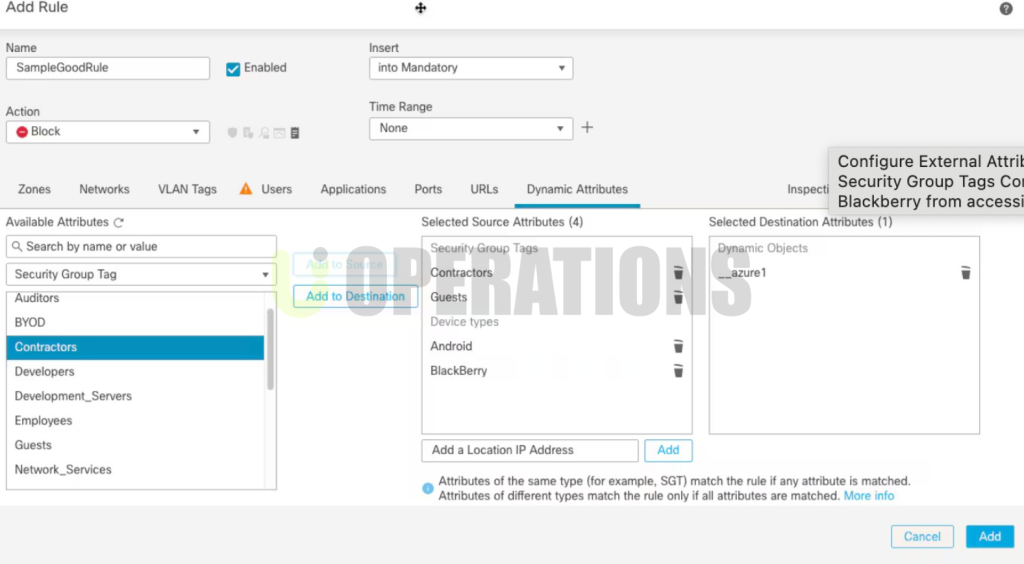
- Security Policy Migration:We migrated and synchronized security policies, NAT rules, and application policies across both firewalls to ensure consistency and protection during failovers.
- Routing Protocols:We configured dynamic routing protocols like OSPF or BGP to ensure that the routing information was updated automatically and correctly during failover.
- Virtual Routers:We set up virtual routers on both firewalls to ensure that routing and network traffic continued to flow without interruption, regardless of which unit was Active.
Step 4: Test and Validation
- Failover Testing:We conducted extensive failover tests by manually shutting down the Active firewall to verify that the Standby unit took over without any noticeable service interruptions.
- Performance Monitoring:We monitored the performance of both the Active and Standby firewalls during failover events to ensure that there was no significant latency or packet loss.
- Verification of Session Sync:Real-world traffic tests were performed to ensure that session synchronization was functioning correctly and that active sessions were not disrupted during failover.
- HA Logging and Alerting:We set up centralized logging and alerting for HA-related events to ensure that the client could be notified of any issues or failover events in real time.
05
Post-Deployment and Optimization
Monitoring and Troubleshooting:
- Real-Time Monitoring:We implemented continuous monitoring through Cisco Firepower Management Center (FMC) to track the health and status of the HA pair, providing the client with visibility into the system.
- Troubleshooting:We addressed minor issues such as misconfigured routing or minor connectivity issues, fine-tuning settings to improve failover times and minimize potential disruptions.
- Documentation:Detailed documentation was provided to the client, including network diagrams, configuration settings, troubleshooting procedures, and best practices for managing HA environments.
Performance Tuning:
- Failover Time Optimization:We adjusted HA configuration settings to ensure failover times were within the client’s target window (30-60 seconds).
- Load Balancing:If applicable, we configured load balancing within the HA setup to distribute traffic evenly between the firewalls during normal operation.
06
Challenges and Solutions
- Challenge 1: HA Link Failure During Setup
- Solution:We resolved issues with intermittent HA link failures by replacing faulty cables and verifying the physical network connectivity between the two firewalls.
- Challenge 2: Session Sync Latency
- Solution:We adjusted session synchronization settings to reduce the timeout period, ensuring that failovers occurred with minimal latency.
- Challenge 3: Policy Synchronization Delays
- Solution:We fine-tuned the policy synchronization process and used FMC to ensure complete and consistent configuration replication across the HA pair.
07
Results and Outcomes
- Successful HA Deployment:The project was successfully completed, with both Cisco FTD firewalls now configured in Active/Standby HA mode, ensuring uninterrupted security and network availability.
- High Availability Achieved:Failover tests demonstrated that the system was able to handle failovers seamlessly, with no noticeable service disruption.
- Improved Network Resilience:The deployment enhanced the network’s resilience, eliminating single points of failure and ensuring the continued operation of critical network services.
- Security Continuity:The client’s security policies were consistently applied across both firewalls, ensuring comprehensive network protection even during failover events.
08
Tools and Technologies Used
- Cisco Firepower Threat Defense (FTD) Firewalls (e.g Firepower 4100 series)
- Cisco Firepower Management Center (FMC) for centralized management
- Dynamic Routing Protocols (OSPF, BGP)
- SNMP, Syslog for monitoring
- HA Configuration Tools within FTD Software
09
Conclusion
The Cisco FTD HA deployment for our client was a complete success, providing a high-availability solution that meets their business continuity and security requirements. With the Active/Standby HA configuration in place, the client now has a highly resilient network infrastructure that ensures minimal downtime and consistent security enforcement. The deployment not only met the client’s immediate needs but also provides a scalable and future-proof solution as their network grows.

