Portfolio Details
Azure Infrastructure Best Practices and Security Assessment
Price: 1500$
Duration: 2 Weeks
01
Project Overview
Our client engaged us to conduct a comprehensive assessment of their Microsoft Azure cloud infrastructure, focusing on security, scalability, performance, and cost optimization. The goal of this project was to evaluate the existing cloud environment, identify any gaps or vulnerabilities, and implement recommended improvements to align the infrastructure with Microsoft Azure’s best practices. The assessment included reviewing security controls, compliance measures, network configurations, and operational efficiency, ensuring that the client’s Azure environment was secure, resilient, and optimized for future growth.
02
Project Objectives
The main objectives of this project were:
- Security Assessment:Identify vulnerabilities and security gaps in the client’s Azure infrastructure and provide remediation strategies.
- Best Practices Alignment:Ensure the Azure environment follows Microsoft’s best practices for security, scalability, performance, cost management, and operational excellence.
- Compliance Review:Ensure the infrastructure meets relevant industry standards and regulatory requirements such as GDPR, HIPAA, PCI-DSS, and others.
- Cost Optimization:Identify opportunities to optimize the Azure infrastructure for cost efficiency, ensuring that resources are effectively allocated without overspending.
- Performance & Scalability:Assess the environment’s performance and scalability to ensure it can support future growth while maintaining high availability and performance.
03
Pre-Deployment Planning
Site Survey & Requirements Gathering:
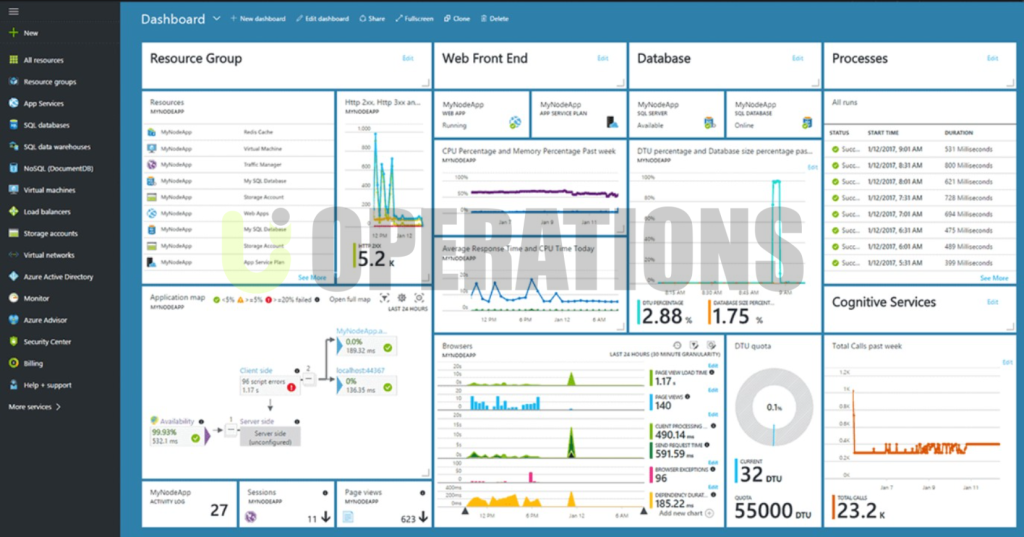
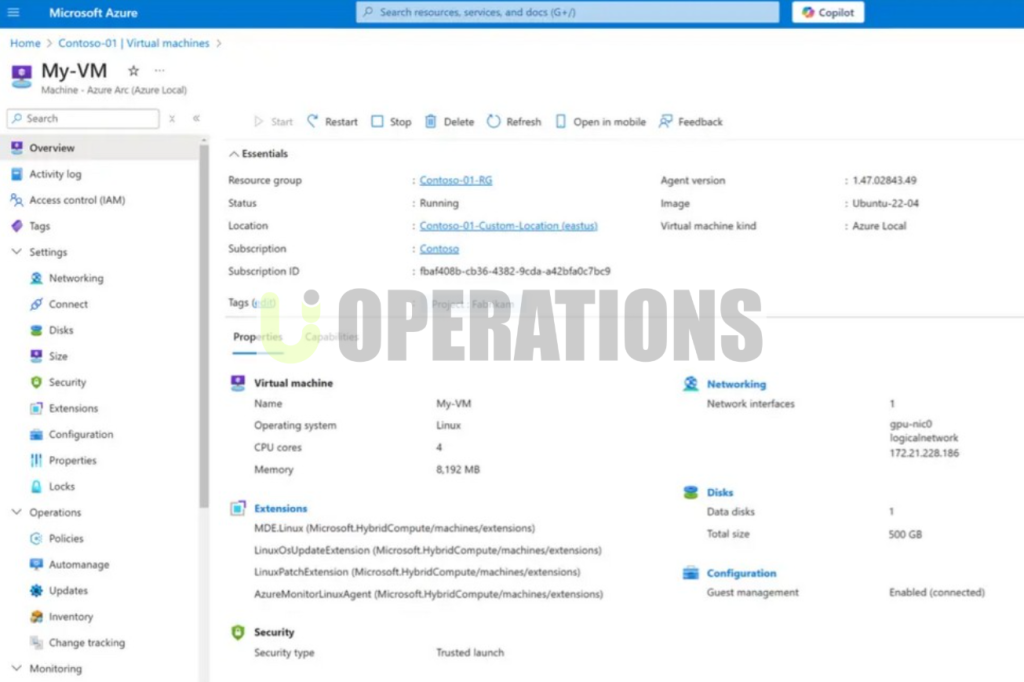
- Current Azure Environment Review:We began by assessing the client’s existing Azure resources, including Virtual Networks (VNets), Network Security Groups (NSGs), storage, Virtual Machines (VMs), identity management, and application configurations.
- Stakeholder Interviews:We worked closely with the client’s cloud, security, and operations teams to understand their current infrastructure setup, challenges, and specific business requirements.
- Scope Definition:The assessment covered critical areas such as identity management, network security, access controls, monitoring, storage configurations, compliance, and cost management.
Assessment Methodology:
- Security Posture Evaluation:We used tools like Azure Security Center, Azure Sentinel, and third-party vulnerability scanners to identify security misconfigurations and vulnerabilities.
- Compliance Checks:We reviewed the environment for compliance with industry regulations, ensuring that controls were in place to protect sensitive data and maintain privacy standards.
- Cost Optimization Review:We used Azure Cost Management tools to review and optimize spending and resource allocation, identifying areas for potential savings.
04
Deployment
Step 1: Security Assessment and Risk Mitigation
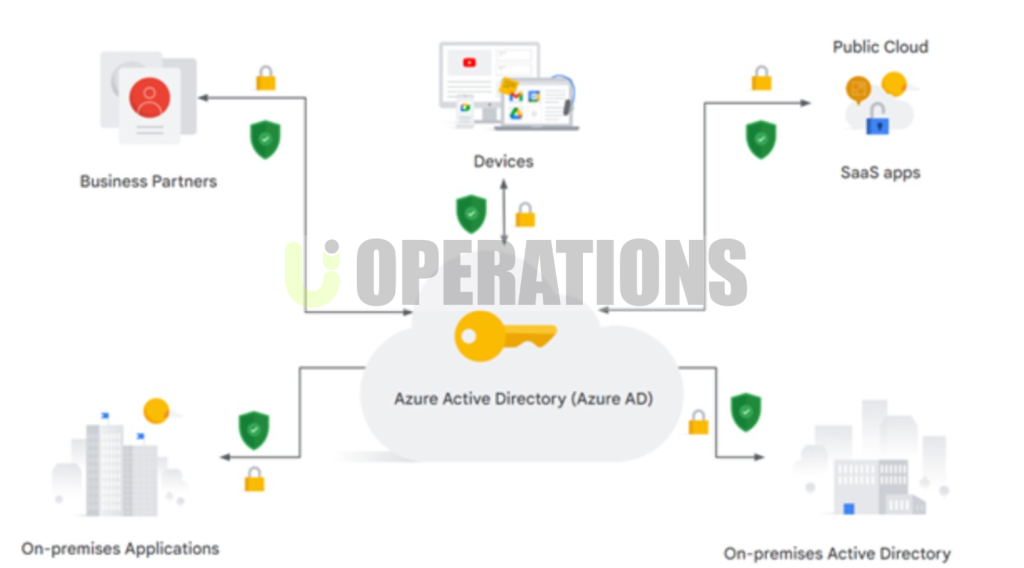
- Identity and Access Management (IAM):We conducted a detailed review of Azure Active Directory (AD) and IAM roles to ensure proper permissions were set. We focused on enforcing the principle of least privilege and ensuring role-based access controls (RBAC) were implemented effectively.
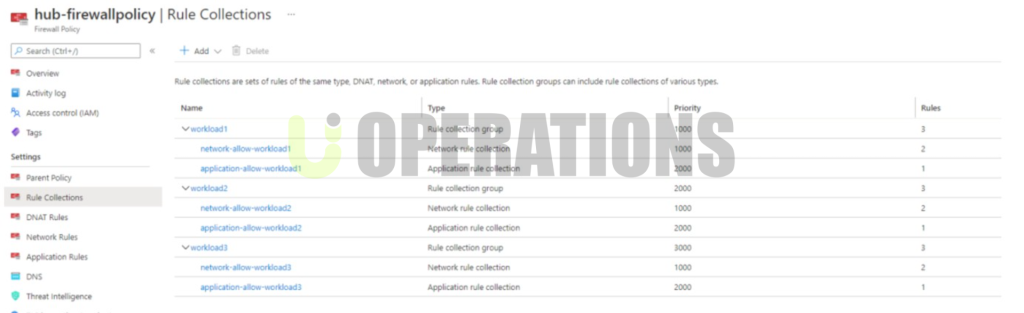
- Network Security:We reviewed the client’s network configurations, ensuring that Network Security Groups (NSGs), Azure Firewall, and Azure Bastion were properly implemented to secure network traffic. We also assessed VNet peering, VPN configurations, and public endpoint exposure.
- Data Protection and Encryption:We ensured that sensitive data was encrypted both at rest and in transit. We reviewed Azure Key Vault configurations for secure key management and ensured that Azure Storage, SQL Databases, and VMs used proper encryption settings.
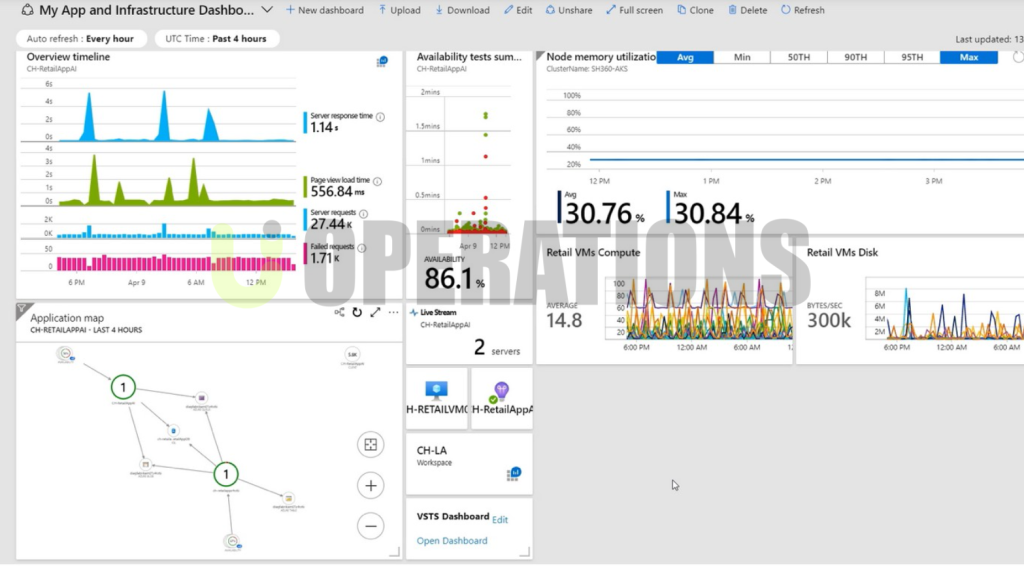
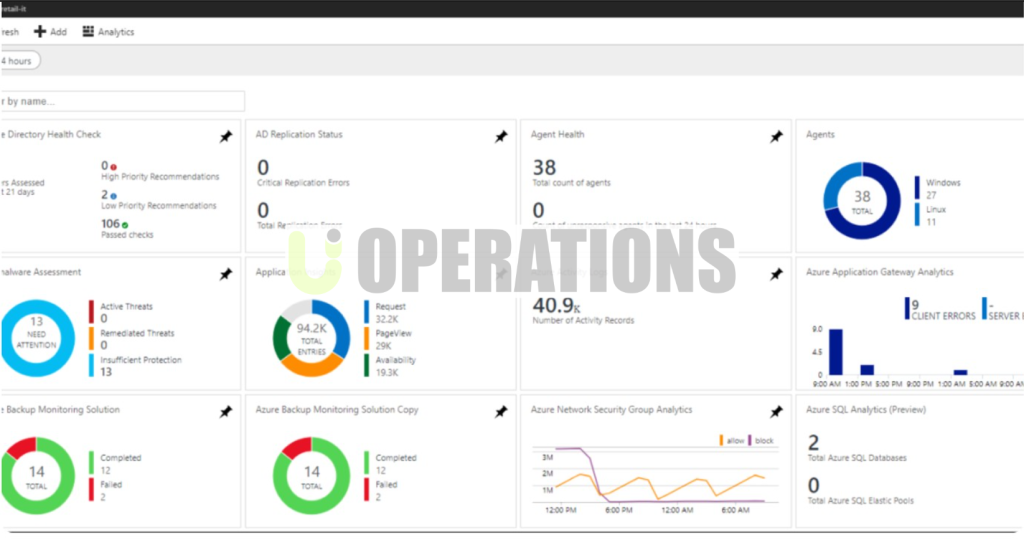
- Logging and Monitoring:We implemented Azure Monitor and Azure Log Analytics for centralized logging, monitoring, and alerting. We ensured that Azure Security Center, Azure Sentinel, and Azure Activity Logs were enabled to track and respond to security events.
- Incident Response Setup:We helped set up automated incident response workflows using Azure Logic Apps and Microsoft Sentinel to detect and respond to potential security incidents quickly.
Step 2: Best Practices Alignment
- Microsoft Azure Well-Architected Framework:We aligned the client’s Azure infrastructure with the five pillars of Microsoft’s Azure Well-Architected Framework:
- Security:Strengthened IAM controls, network security, data protection, and incident response measures.
- Reliability:Ensured high availability by designing fault-tolerant systems, including leveraging Azure Availability Zones, auto-scaling, and redundant storage configurations.
- Performance Efficiency:Optimized the resource usage by right-sizing VMs, using Azure App Service for web applications, and implementing load balancing across regions.
- Cost Optimization:We identified opportunities to use Reserved Instances, Azure Spot VMs, and managed services to reduce overall costs.
- Operational Excellence:Set up monitoring, alerts, and automation to streamline operations and ensure the environment was always optimized.
Step 3: Risk Mitigation and Remediation
- Misconfiguration Fixes:We corrected security misconfigurations such as overly permissive access controls, unsecured storage accounts, and misconfigured network security groups.
- Security Enhancements:We recommended and implemented best practices for secure Azure deployments, such as enabling Azure Defender, using Just-in-Time (JIT) VM access, and implementing multi-factor authentication (MFA) for all administrators.
- Compliance Enhancements:We configured security controls to help the client comply with industry regulations, ensuring that logs were retained for the required duration and data was protected according to regulatory guidelines.
Step 4: Testing & Validation
- Vulnerability Assessment:We conducted vulnerability scans to identify any weaknesses in the configuration of the client’s Azure environment.
- Penetration Testing:A limited penetration test was performed to simulate potential attack scenarios, testing the infrastructure’s resilience against cyber threats.
Compliance Audits: We verified that the necessary compliance controls were in place, including data retention policies, audit logging, and encryption of sensitive data.
05
Post-Deployment and Optimization
Monitoring and Ongoing Security Enhancements:
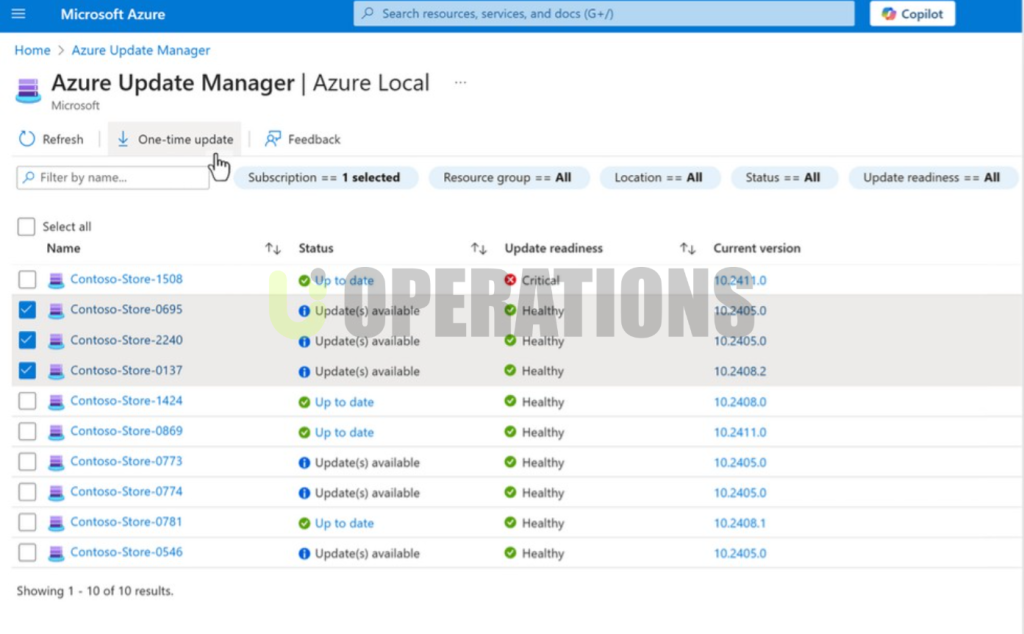
- Continuous Monitoring:We set up Azure Monitor, Azure Security Center, and Azure Sentinel to provide continuous monitoring and alerts for suspicious activities, vulnerabilities, and threats.
- Cost Management:We implemented Azure Cost Management tools to track ongoing costs, set up alerts for budget overruns, and optimize resources for cost efficiency.
- Security Automation:We automated threat detection and response using Azure Logic Apps, Azure Functions, and Microsoft Sentinel, allowing the environment to respond to incidents quickly.
- Documentation:We provided the client with detailed documentation, including security configurations, monitoring setups, incident response procedures, and cost management practices.
Performance and Resource Optimization:
- VM Right-Sizing:We analyzed the client’s virtual machine usage and right-sized instances based on utilization patterns, ensuring cost savings without compromising performance.
- Scalable Architecture:We ensured that auto-scaling groups, load balancers, and redundant architectures were in place to handle increased workloads as the business grows.
06
Challenges and Solutions
- Challenge 1: Overly Broad IAM Permissions
- Solution:We conducted a detailed audit of Azure AD and IAM roles, eliminating excessive permissions and implementing more granular access control using RBAC.
- Challenge 2: Unsecured Public-facing Resources
- Solution:We identified and restricted public-facing resources, ensuring that only necessary services were exposed to the internet and implementing Azure Bastion for secure remote access.
- Challenge 3: Misconfigured Network Security
- Solution:We updated network security groups (NSGs), configured Azure Firewall, and implemented proper segmentation of workloads within VNets to ensure proper access controls and reduced attack surface.
07
Results and Outcomes
- Enhanced Security Posture:The client’s Azure environment now adheres to industry best practices, with stronger identity management, secure networking, data protection, and proactive monitoring in place.
- Cost Savings:The client achieved significant cost reductions by optimizing resources, using Reserved Instances, and moving to more cost-effective Azure services.
- Improved Compliance:The environment is now fully compliant with industry standards, ensuring that the client can meet audit requirements and protect sensitive data.
- Scalable and Reliable Infrastructure:The infrastructure is designed for high availability and can easily scale with the client’s growing needs, ensuring continuity in operations and business growth.
- Operational Excellence:Automated monitoring, incident response, and routine tasks ensure the environment remains secure, performant, and optimized.
08
Tools and Technologies Used
- Microsoft Azure Services:Virtual Machines (VMs), Azure Active Directory (AAD), Azure Security Center, Azure Sentinel, Azure Firewall, Azure Key Vault, Azure Monitor, Azure Cost Management, Azure Logic Apps, Azure Functions
- Security Tools:Azure Defender, Azure Bastion, Just-in-Time (JIT) VM Access, Multi-Factor Authentication (MFA), Azure Security Center
- Compliance Tools:Azure Activity Logs, Azure Audit Logs, Azure Policy, Azure Compliance Manager
- Cost Management Tools:Azure Cost Management, Azure Advisor, Azure Pricing Calculator
09
Conclusion
The Azure Infrastructure Best Practices and Security Assessment project successfully transformed the client’s cloud environment, aligning it with industry best practices for security, scalability, cost optimization, and operational efficiency. By addressing security gaps, optimizing resources, and ensuring compliance, we helped the client build a robust, scalable, and cost-effective Azure infrastructure that is well-positioned for future growth. The implementation of automated monitoring and incident response ensures that the client’s environment remains secure, resilient, and optimized for performance in the long term.