Portfolio Details
AWS Infrastructure Best Practices and Security Assessment
Price: 1500$
Duration: 2.5 Weeks
01
Project Overview
Our client sought our expertise to assess and enhance the security and operational efficiency of their AWS cloud infrastructure. The goal of this project was to ensure that the AWS environment followed industry best practices, optimizing it for security, scalability, and performance while adhering to compliance requirements. We conducted a comprehensive security assessment of the AWS infrastructure, identified areas of improvement, and implemented changes to align with AWS best practices. Our efforts helped the client improve their cloud environment’s security posture, reduce operational risks, and ensure their infrastructure was optimized for future growth.
02
Project Objectives
The key objectives of this project were:
- Security Assessment:To evaluate the existing security measures within the client’s AWS infrastructure, identify potential vulnerabilities, and provide recommendations for remediation.
- Best Practices Alignment:Ensure that the AWS infrastructure follows AWS Well-Architected Framework best practices, including security, cost optimization, performance efficiency, and operational excellence.
- Compliance Adherence:Ensure that the AWS setup complies with relevant industry standards, such as GDPR, HIPAA, PCI-DSS, etc.
- Operational Efficiency:Optimize the infrastructure for better performance, scalability, and cost management, focusing on areas like automation, monitoring, and resource management.
- Risk Mitigation:Minimize the risk of security breaches, data loss, and downtime through proactive measures and implementation of security controls.
03
Pre-Deployment Planning
Site Survey & Requirements Gathering:
- Current AWS Environment Review:We conducted a comprehensive review of the client’s existing AWS infrastructure, examining VPC configurations, IAM roles and policies, EC2 instances, security groups, networking settings, and S3 bucket configurations.
- Stakeholder Interviews:Collaborated with the client’s security, network, and DevOps teams to understand their unique requirements, challenges, and compliance needs.
- Assessment Scope Definition:The scope was clearly defined to focus on areas such as access management, data protection, logging, monitoring, incident response, and scalability.
Assessment Methodology:
- Security Posture Assessment:We conducted a thorough security posture assessment using AWS security tools like AWS Config, AWS Trusted Advisor, and AWS Security Hub to detect vulnerabilities and ensure the infrastructure is securely configured.
- Compliance Checks:We mapped the infrastructure against industry regulations and standards such as GDPR and PCI-DSS to ensure the client’s environment met these requirements.
- Cost Optimization Review:In parallel, we evaluated the infrastructure for cost efficiency, identifying areas where costs could be reduced without impacting performance.
04
Deployment
Step 1: Security Posture Evaluation
- IAM & Access Management:We reviewed and assessed Identity and Access Management (IAM) roles, permissions, and policies. We ensured least privilege access and reviewed policies for compliance with best practices.
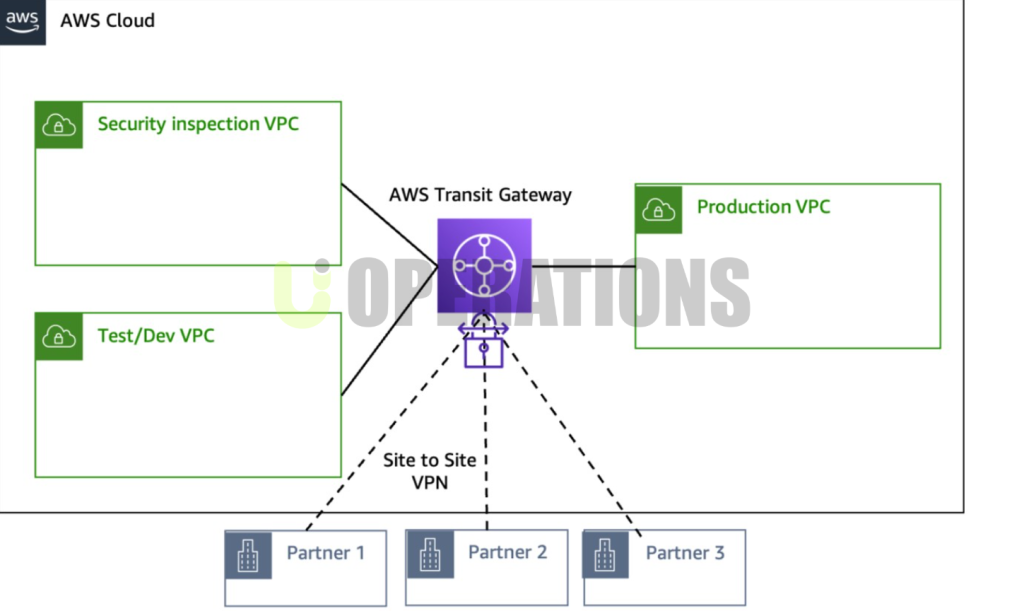
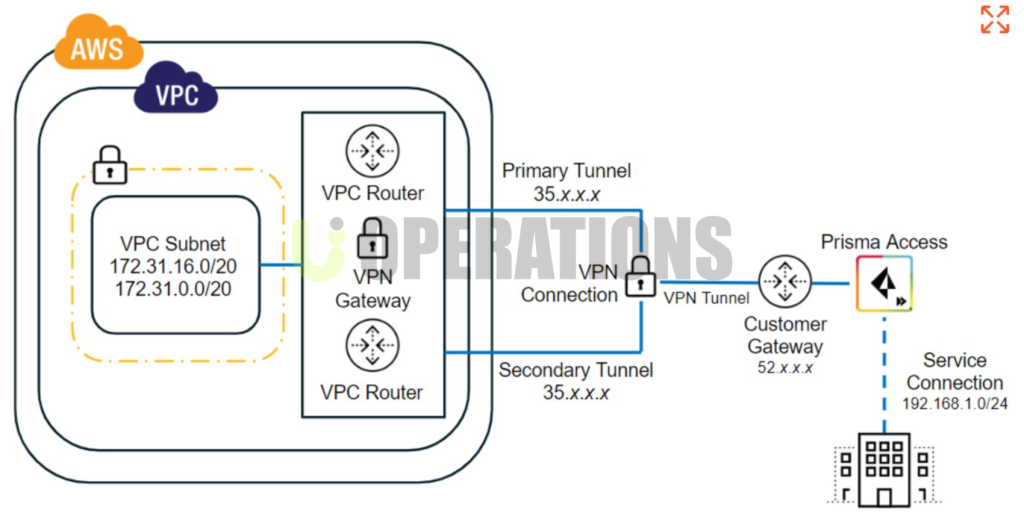
- VPC & Network Configuration:We evaluated the client’s VPC setup to ensure that networking configurations were secure, including the use of private subnets, security groups, and NACLs to limit public exposure.
- Data Protection:We assessed data protection strategies, ensuring encryption of data at rest and in transit, proper access controls on S3 buckets, and encryption configurations on EBS volumes and RDS instances.
- Monitoring and Logging:We ensured that AWS CloudTrail, CloudWatch, and AWS Config were enabled to monitor and log critical activities. Alerts were configured for abnormal or suspicious activities to ensure proactive incident management.
- Incident Response Plan:We reviewed or created an incident response plan, ensuring the client had proper automation and tools to detect and respond to security incidents in a timely manner.
Step 2: Best Practices Alignment
- AWS Well-Architected Framework Review:We conducted an assessment against the AWS Well-Architected Framework, focusing on the five pillars:
- Security:Strengthened controls around identity management, data protection, infrastructure security, and incident response.
- Operational Excellence:Improved monitoring, incident management, and automation strategies to reduce manual interventions.
- Reliability:Enhanced infrastructure design to improve availability, fault tolerance, and disaster recovery capabilities.
- Performance Efficiency:Identified underutilized resources and implemented auto-scaling, right-sizing, and optimization recommendations.
- Cost Optimization:Identified areas of wastage and opportunities for using reserved instances, spot instances, and cost-effective storage solutions.
Step 3: Risk Mitigation & Remediation
- Vulnerability Remediation:We identified any existing vulnerabilities, such as excessive IAM permissions, unsecured S3 buckets, unencrypted data, and potential misconfigurations. These were addressed with targeted fixes.
- Incident Response Automation:Where applicable, we automated security incident response procedures using AWS Lambda and Amazon GuardDuty to detect, respond, and mitigate potential threats in real time.
- Compliance Enhancements:Ensured that security controls were in place to meet compliance requirements, including enabling AWS Artifact for audit reports and ensuring access logging was enabled on all resources.
Step 4: Testing & Validation
- Penetration Testing:Conducted a limited scope penetration test to evaluate the robustness of security measures in place and identify any critical vulnerabilities.
- Failover & Recovery Testing:Validated the failover and disaster recovery procedures by testing backup restoration, region failover scenarios, and data replication.
- Compliance Verification:Ensured that all compliance checks were successfully met, and relevant documentation was in place for audit purposes.
05
Post-Deployment and Optimization
Monitoring and Ongoing Security Enhancements:
- Real-Time Monitoring:Set up AWS CloudWatch and CloudTrail to provide continuous monitoring, ensuring alerts are triggered for unauthorized access attempts, configuration changes, and other critical events.
- Cost Management:Implemented AWS Cost Explorer and Trusted Advisor to continuously monitor the infrastructure for opportunities to optimize costs further.
- Automation and Scaling:We automated routine tasks such as scaling EC2 instances using Auto Scaling Groups and implementing Lambda functions for security incident automation.
- Documentation:Provided the client with comprehensive documentation of the AWS infrastructure, including security configurations, best practices, and a roadmap for continuous improvement.
Performance Tuning and Optimization:
- Cost Optimization:We identified additional cost-saving opportunities, such as consolidating unused resources, switching to Spot Instances, and recommending Reserved Instances for critical workloads.
- Resource Optimization:Right-sized instances and storage solutions for improved performance and reduced costs, ensuring that resources met actual usage patterns.
06
Challenges and Solutions
- Challenge 1: Excessive IAM Permissions
- Solution:We implemented strict role-based access control (RBAC) and ensured that IAM policies adhered to the principle of least privilege. We worked with the client’s teams to ensure that no user had unnecessary administrative access.
- Challenge 2: Unsecured S3 Buckets
- Solution:We conducted an audit of all S3 buckets and implemented proper access control policies, ensuring that all buckets were private unless publicly needed. We enabled logging and versioning for enhanced security.
- Challenge 3: Data Encryption Gaps
Solution: We ensured that all sensitive data was encrypted at rest and in transit using services like AWS Key Management Service (KMS) and SSL/TLS encryption for web applications.
07
Results and Outcomes
- Improved Security Posture:The client’s AWS environment now adheres to AWS best practices, including proper IAM role configurations, encryption, and network security.
- Cost Efficiency:The client achieved significant cost savings by implementing recommendations for cost optimization, including right-sizing, Reserved Instances, and storage optimizations.
- Enhanced Compliance:The infrastructure is now compliant with relevant regulatory standards (e.g., GDPR, HIPAA), and the client is better prepared for audits.
- Scalable and Resilient Infrastructure:By applying AWS Well-Architected Framework principles, the infrastructure is more resilient and scalable, ensuring that it can grow with the client’s needs.
- Operational Excellence:Automated monitoring, incident response, and routine tasks ensure that the infrastructure remains secure, optimized, and well-maintained.
08
Tools and Technologies Used
- AWS Services:EC2, VPC, IAM, CloudTrail, CloudWatch, S3, Lambda, GuardDuty, KMS, Config, Trusted Advisor, AWS Inspector
- Security Tools:AWS Security Hub, AWS Config, AWS WAF, AWS Shield, Penetration Testing Tools
- Compliance Tools:AWS Artifact, AWS Config Rules, PCI-DSS, GDPR, HIPAA
09
Conclusion
The AWS Infrastructure Best Practices and Security Assessment project was a success, providing our client with a more secure, efficient, and scalable cloud infrastructure. By aligning the AWS environment with industry best practices and ensuring compliance with critical security regulations, we helped the client mitigate risks, optimize costs, and improve their overall operational resilience. This engagement has positioned the client’s AWS environment for sustained growth while ensuring data protection, security, and efficiency across their cloud services.