Portfolio Details
Wazuh SIEM Solution Deployment
Price: 1500$
Duration: 2 weeks
01
Project Overview
In response to a client’s request for enhanced security monitoring and log analysis, our team successfully deployed Wazuh, an open-source security monitoring platform, in the client’s infrastructure. Wazuh was chosen for its capability to integrate with existing systems, provide real-time threat detection, vulnerability analysis, and ensure compliance with industry regulations. The implementation of Wazuh significantly strengthened the client’s security posture by improving visibility into their infrastructure and ensuring rapid response to potential security incidents.
02
Client Requirements
Our client, a mid-sized financial services company, approached us with the following specific requirements:
- Real-time Security Monitoring: The client needed a centralized solution to monitor and detect security threats in real time across their entire network infrastructure.
- Log Management and Analysis: The client required a robust log management system capable of aggregating, storing, and analyzing logs from various sources such as firewalls, servers, and endpoints.
- Compliance Needs: As a financial institution, the client must comply with industry standards such as PCI-DSS, GDPR, and SOX. The solution needed to help them meet these compliance requirements by providing audit trails and generating compliance reports.
- Cost-Effective Solution: The client expressed interest in an open-source security solution that could deliver enterprise-grade functionality while being mindful of budget constraints.
- Scalability and Integration: The solution needed to scale as the client’s infrastructure grew and seamlessly integrate with their existing security tools (e.g., SIEM, intrusion detection systems).
03
Solution Approach
- Initial Assessment and Planning
- We performed an in-depth assessment of the client’s infrastructure, identifying key systems and applications that required monitoring.
- We reviewed their existing security tools and processes to ensure that Wazuh could integrate smoothly with their environment.
- We developed a deployment plan, ensuring minimal disruption to ongoing operations.
04
Deployment Steps
Step 1: Wazuh Manager Setup
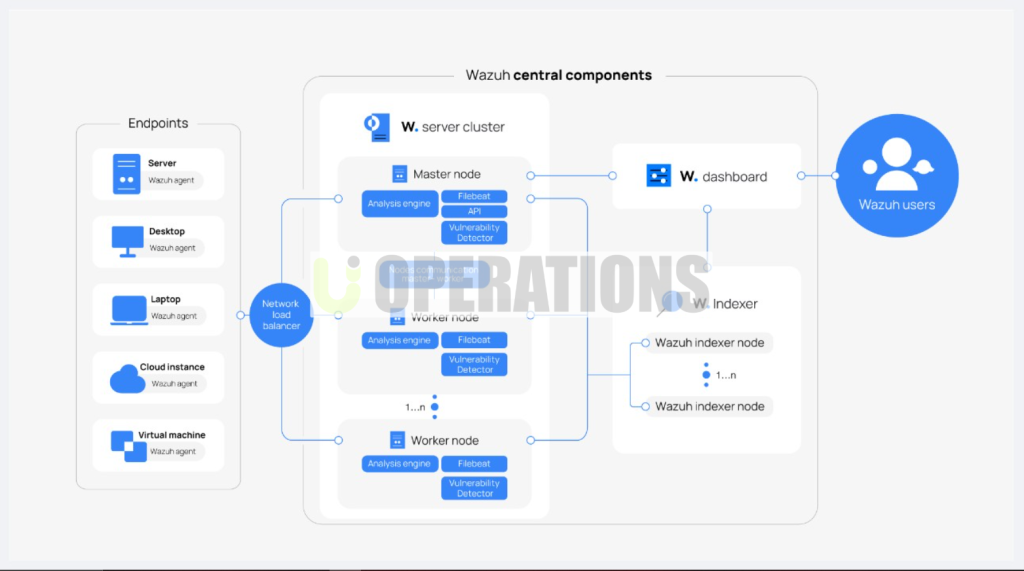
- We began by setting up the Wazuh Manageron a dedicated server. The Wazuh Manager is the core component responsible for managing agents, storing logs, and processing security events.
- We configured the manager to optimize performance for the client’s environment, including allocating sufficient resources for log storage and event processing.
Step 2: Agent Installation
- Wazuh Agentswere deployed across the client’s infrastructure, including endpoints, servers, firewalls, and databases, to collect logs and security data.
- The agent installation process involved pushing the Wazuh agent to each monitored system and ensuring that the agent was properly communicating with the Wazuh Manager.
- We used automated deployment scripts to streamline the installation and minimize manual effort.
Step 3: Log Collection and Integration
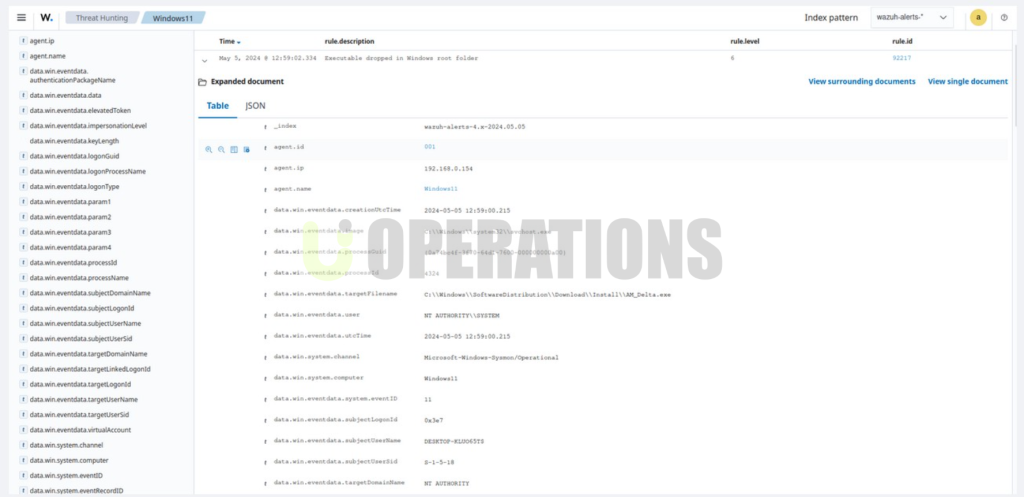
- We configured the Wazuh agents to collect logs from various data sources, including system logs, application logs, firewall logs, and intrusion detection system (IDS) logs.
- We integrated Wazuh with the client’s SIEM platform(such as the Elastic Stack) to centralize log collection and analysis, ensuring that logs from all sources were aggregated and stored in one location.
Step 4: Configuration of Security Rules and Alerts
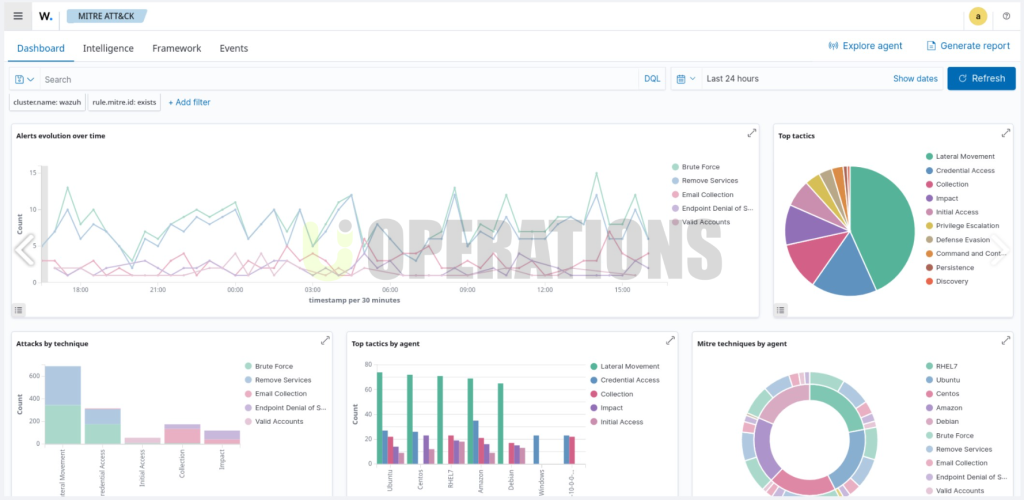
- We configured Wazuh’s pre-built security rules to detect various security threats, including malware, unauthorized access attempts, and network intrusions.
- We customized and fine-tuned rules to suit the specific needs of the client, adjusting thresholds and sensitivities to reduce false positives and ensure that only meaningful alerts were generated.
Step 5: Compliance Setup and Configuration
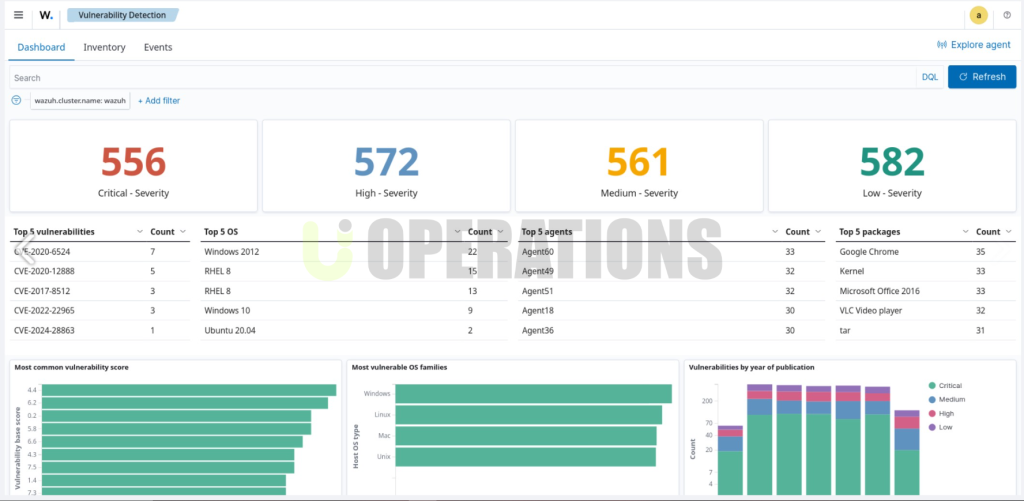
- We enabled Wazuh’s compliance moduleto ensure that the client could easily meet industry regulations such as PCI-DSS, GDPR, and SOX.
- Custom compliance rules were configured to automatically generate reports on security controls, providing the client with a clear audit trail and documentation for regulatory purposes.
Step 6: Performance Optimization and Tuning
- We optimized both the Wazuh Manager and the agent configurations to ensure the system performed efficiently under the expected load. This included adjusting the logging frequency, fine-tuning event processing, and ensuring the system could handle large volumes of log data.
- Load balancing and failover configurations were implemented to ensure high availability and resilience of the Wazuh platform.
Step 7: Testing and Validation
- After completing the setup, we performed a series of tests to validate the deployment. These tests included simulating security incidents (e.g., unauthorized access attempts) to verify that Wazuh would detect and alert the client in real time.
- We also tested the integration with the SIEM and other security tools to ensure seamless data flow.
Step 8: Training and Knowledge Transfer
- We conducted training sessions with the client’s security team to ensure they understood how to use Wazuh effectively, including how to manage alerts, review logs, and configure rules.
- A comprehensive user guide and documentation were provided to facilitate ongoing system management.
Step 9: Handover and Ongoing Support
- After the deployment was completed and thoroughly tested, we handed over full control of the Wazuh platform to the client’s security team.
- We set up a support plan to assist with any future issues, ensuring they had access to technical assistance and software updates.
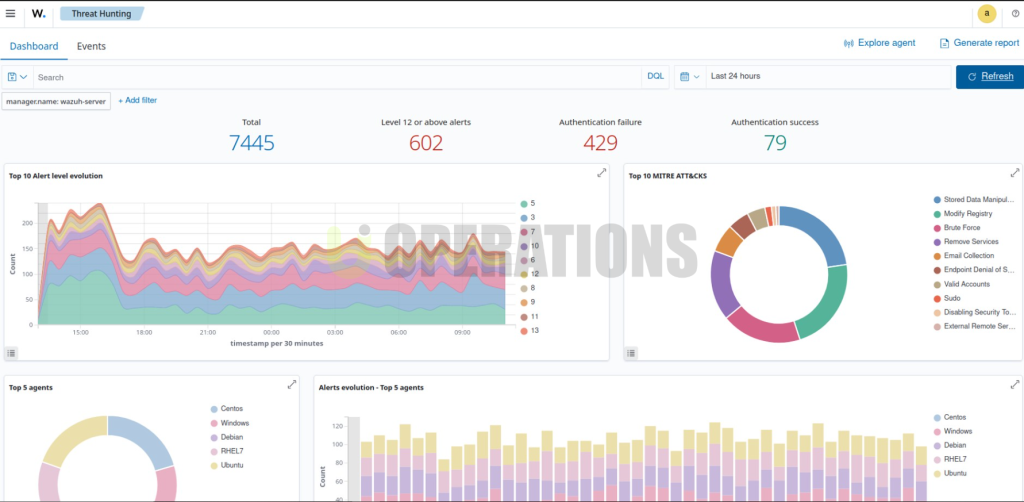
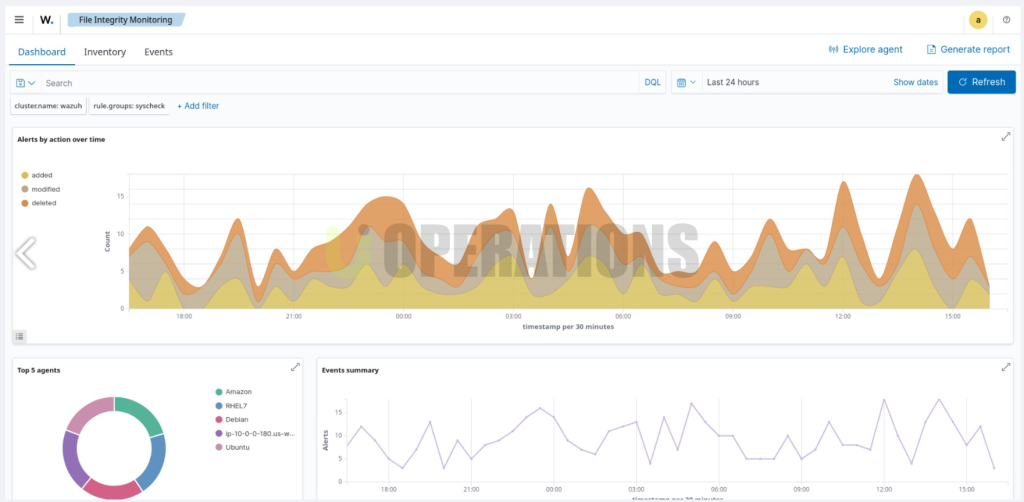
05
Results and Benefits
The Wazuh deployment provided the following key benefits to the client:
- Enhanced Security Posture: The client gained real-time visibility into their network, enabling quicker detection of security incidents and faster response times.
- Compliance Assurance: Wazuh’s automated compliance reporting helped the client meet regulatory requirements and reduce the risk of non-compliance penalties.
- Centralized Log Management: By aggregating logs from various sources, Wazuh enabled the client to streamline their log management processes and gain better insights into their infrastructure.
- Scalable Solution: The Wazuh deployment was designed to scale with the client’s growing infrastructure, ensuring continued security and performance as their environment evolves.
- Cost Savings: As an open-source solution, Wazuh provided a cost-effective alternative to proprietary security tools, significantly reducing the client’s security monitoring costs.
06
Challenges Overcome
During the deployment process, our team encountered several challenges, including:
- Integration with Existing Systems: Ensuring smooth integration with the client’s existing SIEM and security tools required careful configuration and testing. Our team worked closely with the client’s IT staff to ensure seamless data flow between Wazuh and their other security systems.
- Performance Optimization: Tuning the system to handle large volumes of log data from multiple sources required optimizing agent configurations and ensuring the Wazuh Manager could handle the processing load without performance degradation.
- Training and Knowledge Transfer: Ensuring the client’s internal team was fully capable of managing and maintaining the Wazuh deployment required comprehensive training and a well-documented handover process.
07
Conclusion
The deployment of Wazuh in the client’s infrastructure was a resounding success. By leveraging Wazuh’s comprehensive security monitoring and compliance features, we were able to meet the client’s needs for real-time monitoring, log management, and regulatory compliance while providing a cost-effective solution. The client is now better equipped to detect and respond to security threats and maintain compliance with industry regulations.
We look forward to continuing our partnership with the client, providing ongoing support and ensuring their infrastructure remains secure and compliant.