Portfolio Details
Palo Alto HA Deployment
Price: 1250$
Duration: 3 DAYS
01
Project Overview
Project Name:
Palo Alto High Availability (HA) DeploymentProject Overview:
We were tasked by our client to deploy a High Availability (HA) solution using Palo Alto Networks firewalls, with the primary objective of ensuring network redundancy, fault tolerance, and uninterrupted uptime. The client required a solution that would guarantee minimal downtime and robust security measures, even during maintenance or hardware failures. Our goal was to configure and implement an Active/Passive HA pair of Palo Alto Networks PA-5220 firewalls to meet the client’s business continuity objectives. This project involved several phases, including detailed planning, design, implementation, and rigorous testing, ultimately improving the client’s security infrastructure and ensuring minimal disruption in case of failure.
02
Project Objectives
The key objectives for the project were outlined as follows:
- Network Redundancy:Our client required that their network remain operational even during hardware failure or scheduled maintenance. This was achieved by configuring a high availability solution between two Palo Alto firewalls.
- Minimal Downtime:The client wanted to ensure that in the event of a firewall failure, failover would be seamless with minimal disruption.
- Security Optimization:Maintaining the integrity of the client’s security policies while ensuring that these policies are consistently enforced across both firewalls was a top priority.
- Scalability:The client needed a scalable solution that would allow for easy expansion without impacting performance. We designed the solution to accommodate future device additions.
03
Pre-Deployment Planning
Site Survey & Requirements Gathering:
- Current Network Architecture Review:We first conducted a comprehensive review of the client’s existing network architecture and firewall configuration to identify areas that could benefit from redundancy.
- Stakeholder Interviews:We worked closely with the client’s network and security teams to define specific HA requirements, such as failover time expectations, load balancing preferences, and security policy requirements.
- Device Selection:Based on the client’s network load and performance requirements, we selected appropriate Palo Alto Networks models, specifically the PA-5200 series firewalls.
Design & Architecture:
- High Availability Topology:We designed a solution using an Active/Passive HA setup, where the primary unit was configured as the Active firewall and the secondary unit as Passive.
- HA Requirements:
- Redundant Management:We ensured redundant management interfaces to guarantee continuous remote access.
- HA Ports:We configured dedicated HA ports for control and data link between the firewalls, ensuring efficient communication.
- Session Synchronization:To minimize service disruption, we designed the HA solution to synchronize sessions between the firewalls.
- IP Addressing & Routing:
- Floating IPs:We configured floating IP addresses to enable seamless failover between the devices.
- Routing Protocols:Dynamic routing protocols, such as OSPF or BGP, were set up to ensure automatic failover without manual intervention.
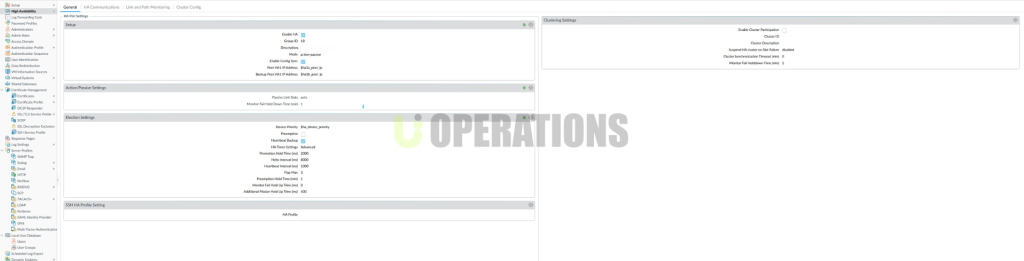
- HA Configuration:We synchronized policies and configurations across the devices and configured link monitoring for physical interfaces and election criteria for the Active and Passive firewalls.
04
DEPLOYMENT
Step 1: Hardware & Software Setup
- Firewall Installation:We physically installed two Palo Alto firewalls (model PA-5200) in the client’s data center.
- PAN-OS Version:We ensured that the latest stable PAN-OS version was deployed to ensure full compatibility with HA features.
- Initial Configuration:
- Set up management interfaces and static IP configurations.
- Configured the HA link between the two firewalls using the dedicated HA port.
- Verified both firewalls were on the same software version and synchronized.
Step 2: HA Configuration
- HA Pairing:We established the HA pair by linking the two firewalls using the dedicated HA port, ensuring they were synchronized and ready for operation.
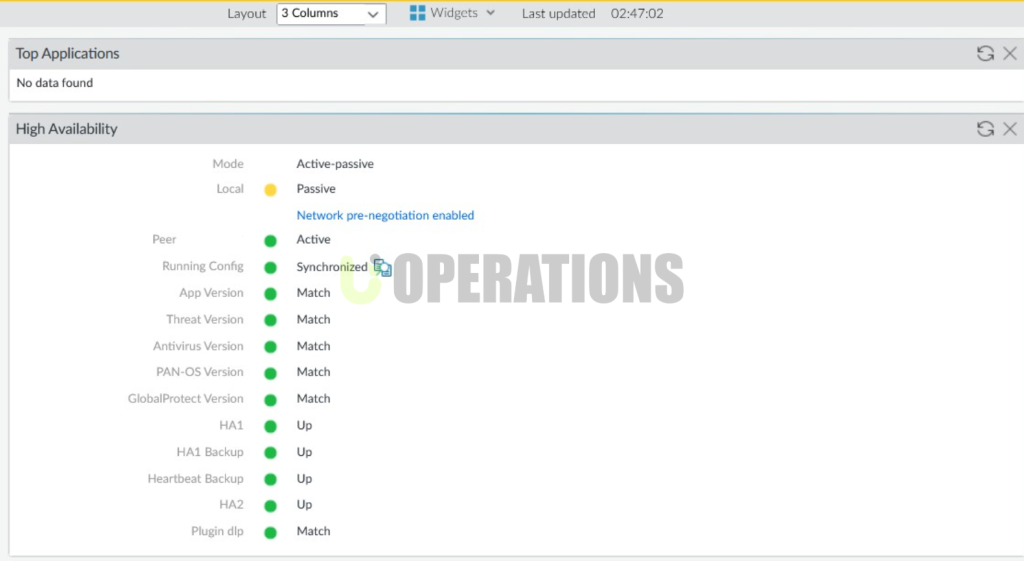
- HA Mode Selection:Active/Passive mode was selected, in line with the client’s requirements for primary and secondary firewalls.
- Session Sync & Stateful Failover:We ensured session synchronization was configured for stateful failover, minimizing session disruption during failover.
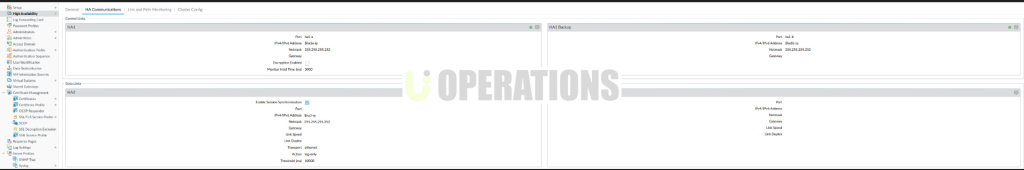
- Health Monitoring:We configured health monitoring, including interface health checks and system monitoring, to ensure automatic failover in the event of link or hardware failure.
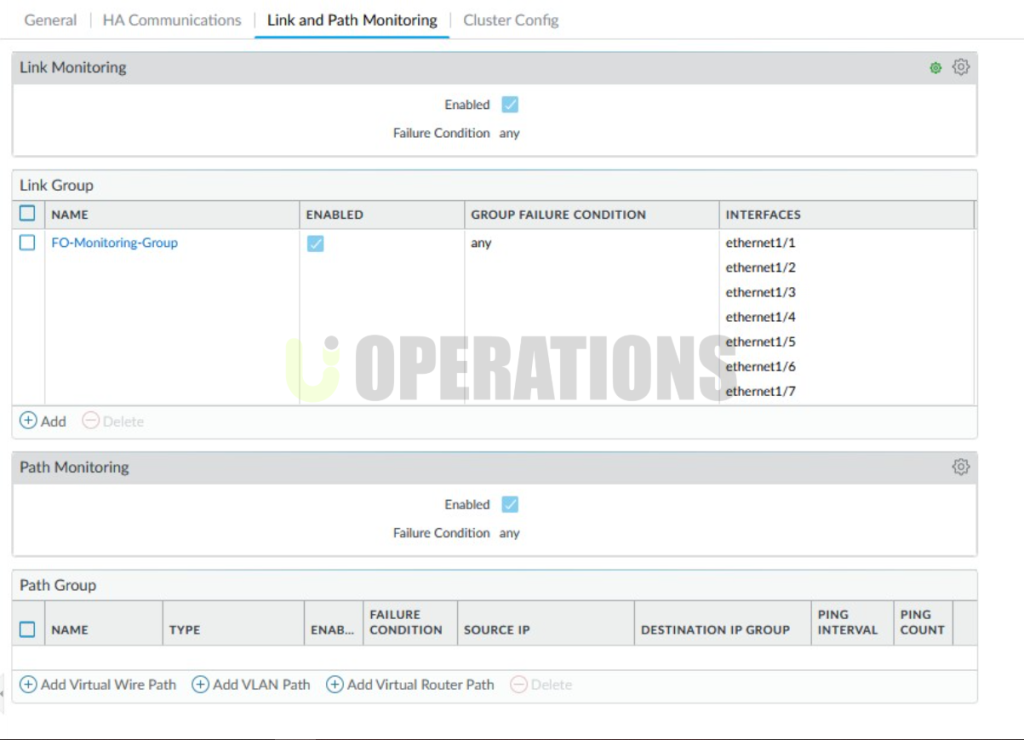
Step 3: Policy and Rule Configuration
- Security Policy Migration:We configured identical security policies, NAT rules, and application rules on both firewalls to ensure uniform enforcement across the HA pair.
- Routing Protocols:Dynamic routing protocols (e.g., OSPF) were implemented to allow seamless failover and traffic distribution in the event of device failure.
- Virtual Routers:We configured virtual routers on both firewalls to ensure consistent routing functionality across the HA pair.
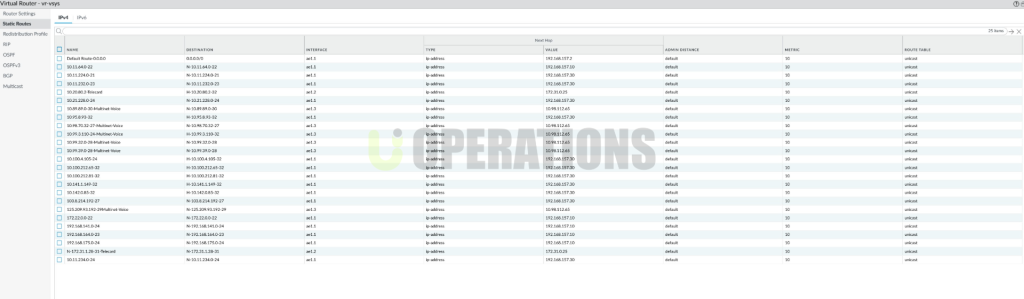
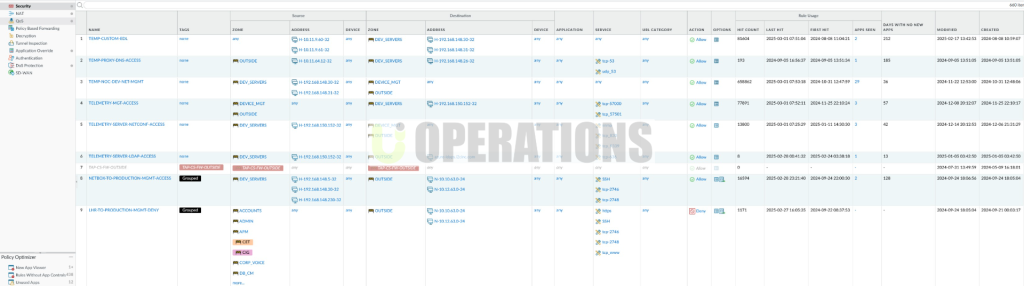
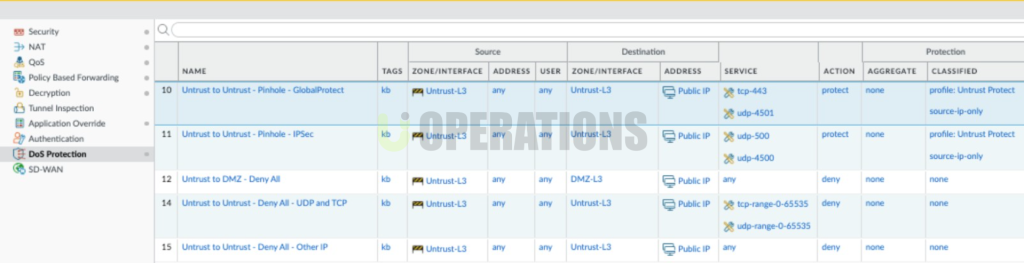
Step 4: Test and Validation
- Failover Testing:We conducted manual failover tests by shutting down the active firewall to ensure the passive unit took over without noticeable disruption to the network.
- Performance Monitoring:We continuously monitored the performance of both firewalls during failover, ensuring that traffic continued without latency or loss.
- Verification of Session Sync:Real-world application traffic tests were performed to ensure that session synchronization was functioning properly and that there was no disruption in active sessions during failover.
- High Availability Logging:We centralized logs from both firewalls, and set up alerts for any HA-related events to ensure proper monitoring.
05
Post-Deployment and Optimization
Monitoring and Troubleshooting:
- Real-Time Monitoring:We implemented real-time monitoring using Palo Alto Panorama and SNMP to keep track of system health and failover status.
- Troubleshooting:We handled any initial troubleshooting tasks, such as addressing minor connectivity issues and refining failover time by adjusting HA settings.
- Documentation:Detailed network diagrams and documentation for the HA deployment were provided to the client, including troubleshooting guides and best practices for failover management.
Performance Tuning:
- Failover Time Optimization:We fine-tuned HA settings to achieve optimal failover times within the 30-60 second range, as per the client’s expectations.
- Load Balancing:If using Active/Active HA, we adjusted load balancing algorithms to ensure even distribution of traffic between the firewalls.
06
Challenges and Solutions
- Challenge 1: HA Link Failure During Setup
- Solution:We replaced faulty cables and verified physical network connectivity to eliminate intermittent link failures.
- Challenge 2: Session Sync Latency
- Solution:We adjusted session synchronization settings and reduced the timeout period to minimize failover delays.
- Challenge 3: Policy Propagation Delays
- Solution:We rechecked policy synchronization settings and tested the configuration using Panorama to ensure complete replication of policies across the HA pair.
07
Results and Outcomes
- Successful HA Deployment:The project was completed successfully, with both firewalls now configured in Active/Passive HA mode.
- High Availability Achieved:The failover tests showed that the firewall pair was able to handle failover seamlessly, with no disruption to the network.
- Improved Network Resilience:The deployment significantly enhanced the network’s resilience, ensuring no single point of failure.
- Security Continuity:The client’s security policies were consistently applied across both firewalls, ensuring uninterrupted protection for the network.
08
Tools and Technologies Used
- Palo Alto Networks Firewalls (e.g., PA-5200 Series)
- PAN-OS Software
- Palo Alto Panorama for centralized management
- Dynamic Routing Protocols (OSPF, BGP)
- SNMP, Syslog for monitoring
- HA Configuration Tools within PAN-OS
09
Conclusion
The deployment of Palo Alto HA for our client was a resounding success. The High Availability solution now ensures continuous network uptime, providing resilience in case of firewall failure, while maintaining security policy enforcement across the organization. With the project completed as per the client’s requirements, the client’s business continuity objectives have been fully met, ensuring a secure and reliable network infrastructure for years to come.