Portfolio Details
Cortex XDR Deployment and Integration
Price: 1600$
Duration: 2 Weeks
01
Introduction
Cortex XDR is a comprehensive detection and response platform designed to protect endpoints, networks, and cloud environments from a wide range of threats. The solution offers a combination of advanced analytics, machine learning, and automated response capabilities to provide robust cybersecurity protection. This document outlines the deployment and integration of Cortex XDR, which was done in response to a specific client’s cybersecurity requirements.
02
Client Requirements
The client approached us with a series of needs to enhance their security posture. Their specific requirements included:
- Comprehensive Endpoint Protection: The client was looking for a solution that could offer advanced detection, prevention, and response capabilities for endpoints, such as laptops, desktops, and mobile devices.
- Centralized Management: The client requested a centralized platform to manage and monitor security events across all devices, users, and networks. This included integration with their existing SIEM (Security Information and Event Management) systems for streamlined reporting and alerting.
- Scalability and Flexibility: The solution needed to scale seamlessly across their global network of devices, adapting to their growing infrastructure and diverse operational environments.
- Integration with Existing Security Tools: The client had multiple existing security tools, such as firewalls, anti-malware software, and threat intelligence systems. They requested that Cortex XDR integrate with these tools to create a unified, holistic approach to threat detection and mitigation.
- Advanced Threat Detection: The client required advanced threat detection capabilities that leveraged machine learning and behavioral analytics to identify sophisticated threats and reduce false positives.
- Cloud Security: As the client was moving more of their infrastructure to the cloud, they needed a solution that could provide security for cloud-based workloads, including SaaS applications, containerized environments, and cloud storage.
- Incident Response Automation: The client wanted automated response capabilities that would allow for rapid containment and remediation of security incidents, minimizing downtime and reducing the impact on operations.
03
Deployment Process
- Pre-Deployment Planning
The deployment process began with a thorough assessment of the client’s existing IT infrastructure, security posture, and specific requirements. This step was critical in ensuring that Cortex XDR would integrate smoothly into their environment.
- Environment Assessment: We reviewed the client’s endpoint configurations, network topology, and existing security tools.
- Requirement Mapping: We aligned the features of Cortex XDR with the client’s needs, ensuring that the deployment would address all their cybersecurity objectives.
- Risk Assessment: A detailed risk analysis was conducted to identify any potential vulnerabilities in the client’s systems that could be mitigated by the deployment of Cortex XDR.
- Configuration and Customization
Once the assessment phase was completed, we began configuring the Cortex XDR platform to meet the client’s requirements.
- Endpoint Deployment: The Cortex XDR agent was deployed to all endpoints, including laptops, desktops, and mobile devices, ensuring that all devices were monitored for potential security threats.
- SIEM Integration: The solution was integrated with the client’s SIEM system, enabling seamless log forwarding and real-time security event monitoring.
- Cloud Integration: Cloud-based environments were configured with the appropriate settings for Cortex XDR to monitor and protect cloud workloads.
- Testing and Validation
After deployment, we conducted rigorous testing to ensure that the solution was functioning correctly and meeting the client’s specific needs:
- Simulated Attacks: We conducted a series of simulated attacks to test the detection and response capabilities of the system, ensuring that the solution could effectively identify and mitigate threats.
- Performance Monitoring: We monitored system performance to ensure that there were no significant impacts on device or network performance.
- Training and Knowledge Transfer
In parallel with the deployment process, we provided the client’s security team with training on how to use Cortex XDR effectively. This included:
- Endpoint Protection Management: Training on how to manage endpoint agents, monitor alerts, and configure policies.
- Incident Response Playbooks: Guidance on how to use Cortex XDR’s automated response capabilities to rapidly contain and resolve incidents.
- Reporting and Analytics: Education on how to generate reports and analyze threat data to improve their security posture.
- Ongoing Support and Maintenance
Post-deployment, we provided the client with ongoing support, including regular updates and performance reviews. We also assisted with troubleshooting any issues that arose after the system went live.
Integration with Existing Security Infrastructure
One of the client’s primary concerns was ensuring that Cortex XDR would work seamlessly with their existing security tools. As such, we took the following steps:
- Integration with Firewall Systems: Cortex XDR was configured to integrate with the client’s firewall infrastructure, enabling threat intelligence sharing between the two systems.
- Anti-Malware Software Integration: We ensured that Cortex XDR did not conflict with the client’s existing anti-malware software, allowing both systems to work together without redundant protection layers.
- Threat Intelligence Feeds: The integration with third-party threat intelligence sources allowed Cortex XDR to enrich its detection capabilities with external threat data, improving its ability to detect emerging threats.
04
Integration with Existing Security Infrastructure
One of the client’s primary concerns was ensuring that Cortex XDR would work seamlessly with their existing security tools. As such, we took the following steps:
- Integration with Firewall Systems: Cortex XDR was configured to integrate with the client’s firewall infrastructure, enabling threat intelligence sharing between the two systems.
- Anti-Malware Software Integration: We ensured that Cortex XDR did not conflict with the client’s existing anti-malware software, allowing both systems to work together without redundant protection layers.
- Threat Intelligence Feeds: The integration with third-party threat intelligence sources allowed Cortex XDR to enrich its detection capabilities with external threat data, improving its ability to detect emerging threats.
05
Key Benefits Delivered
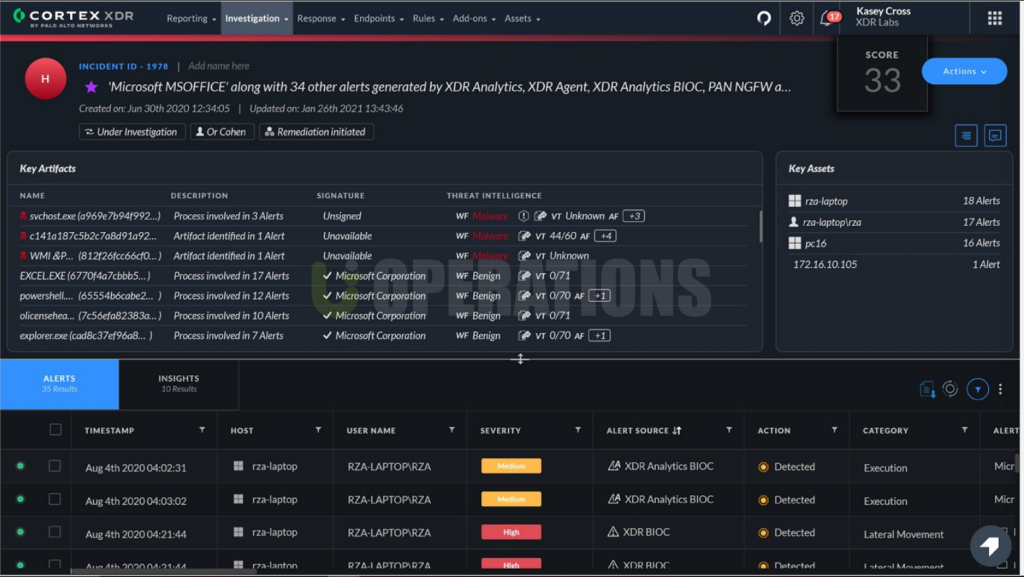
- Comprehensive Threat Detection: The client benefited from advanced machine learning and behavioral analytics that helped detect sophisticated threats across their endpoints and cloud infrastructure.
- Reduced Response Times: The automation of incident response significantly reduced response times, enabling the client to contain and remediate threats faster.
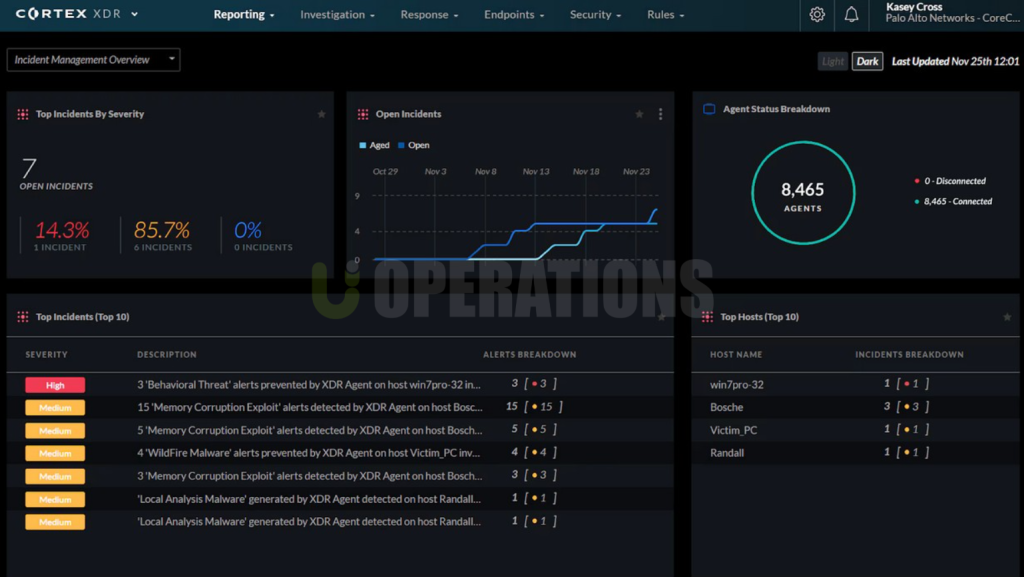
- Improved Visibility: The centralized dashboard provided the client with greater visibility into their security landscape, helping them make more informed decisions.
- Seamless Integration: Cortex XDR was successfully integrated with the client’s existing security infrastructure, enhancing their overall security posture without requiring a complete overhaul of their existing tools.
- Scalability: The solution scaled seamlessly as the client’s infrastructure grew, allowing them to maintain robust security across a growing number of endpoints and cloud environments.
06
Conclusion
Cortex XDR proved to be an ideal solution for the client, meeting their requirements for endpoint protection, advanced threat detection, automated response, and integration with existing security systems. Through careful planning, configuration, and testing, the deployment was successful, and the client now benefits from a comprehensive and scalable security platform that addresses their current and future cybersecurity needs.